ATS Integration : An In-Depth Guide With Key Concepts And Best Practices
Read more


Read more

All the hot and popular Knit API resources
.webp)
Sage 200 is a comprehensive business management solution designed for medium-sized enterprises, offering strong accounting, CRM, supply chain management, and business intelligence capabilities. Its API ecosystem enables developers to automate critical business operations, synchronize data across systems, and build custom applications that extend Sage 200's functionality.
The Sage 200 API provides a structured, secure framework for integrating with external applications, supporting everything from basic data synchronization to complex workflow automation.
In this blog, you'll learn how to integrate with the Sage 200 API, from initial setup, authentication, to practical implementation strategies and best practices.
Sage 200 serves as the operational backbone for growing businesses, providing end-to-end visibility and control over business processes.
Sage 200 has become essential for medium-sized enterprises seeking integrated business management by providing a unified platform that connects all operational areas, enabling data-driven decision-making and streamlined processes.
Sage 200 breaks down departmental silos by connecting finance, sales, inventory, and operations into a single system. This integration eliminates duplicate data entry, reduces errors, and provides a 360-degree view of business performance.
Designed for growing businesses, Sage 200 scales with organizational needs, supporting multiple companies, currencies, and locations. Its modular structure allows businesses to start with core financials and add capabilities as they expand.
With built-in analytics and customizable dashboards, Sage 200 provides immediate insights into key performance indicators, cash flow, inventory levels, and customer behavior, empowering timely business decisions.
Sage 200 includes features for tax compliance, audit trails, and financial reporting standards, helping businesses meet regulatory requirements across different jurisdictions and industries.
Through its API and development tools, Sage 200 can be tailored to specific industry needs and integrated with specialized applications, providing flexibility without compromising core functionality.
Before integrating with the Sage 200 API, it's important to understand key concepts that define how data access and communication work within the Sage ecosystem.
The Sage 200 API enables businesses to connect their ERP system with e-commerce platforms, CRM systems, payment gateways, and custom applications. These integrations automate workflows, improve data accuracy, and create seamless operational experiences.
Below are some of the most impactful Sage 200 integration scenarios and how they can transform your business processes.
Online retailers using platforms like Shopify, Magento, or WooCommerce need to synchronize orders, inventory, and customer data with their ERP system. By integrating your e-commerce platform with Sage 200 API, orders can flow automatically into Sage for processing, fulfillment, and accounting.
How It Works:
Sales teams using CRM systems like Salesforce or Microsoft Dynamics need access to customer financial data, order history, and credit limits. Integrating CRM with Sage 200 ensures sales representatives have complete customer visibility.
How It Works:
Manufacturing and distribution companies need to coordinate with suppliers through procurement portals or vendor management systems. Sage 200 API integration automates purchase order creation, goods receipt, and supplier payment processes.
How It Works:
Organizations with multiple subsidiaries or complex group structures need consolidated financial reporting. Sage 200 API enables automated data extraction for consolidation tools and business intelligence platforms.
How It Works:
Field sales and service teams need mobile access to customer data, inventory availability, and order processing capabilities. Sage 200 API powers mobile applications for on-the-go business operations.
How It Works:
Financial teams spend significant time matching bank transactions with accounting entries. Integrating banking platforms with Sage 200 automates this process, improving accuracy and efficiency.
How It Works:
Sage 200 API uses token-based authentication to secure access to business data:
Implementation examples and detailed configuration are available in the Sage 200 Authentication Guide.
Before making API requests, you need to obtain authentication credentials. Sage 200 supports multiple authentication methods depending on your deployment (cloud or on-premise) and integration requirements.
Step 1: Register your application in the Sage Developer Portal. Create a new application and note your Client ID and Client Secret.
Step 2: Configure OAuth 2.0 redirect URIs and requested scopes based on the data your application needs to access.
Step 3: Implement the OAuth 2.0 authorization code flow:
Step 4: Refresh tokens automatically before expiry to maintain seamless access.
Step 1: Enable web services in the Sage 200 system administration and configure appropriate security settings.
Step 2: Use basic authentication or Windows authentication, depending on your security configuration:
Authorization: Basic {base64_encoded_credentials}
Step 3: For SOAP services, configure WS-Security headers as required by your deployment.
Step 4: Test connectivity using Sage 200's built-in web service test pages before proceeding with custom development.
Detailed authentication guides are available in the Sage 200 Authentication Documentation.
IIntegrating with the Sage 200 API may seem complex at first, but breaking the process into clear steps makes it much easier. This guide walks you through everything from registering your application to deploying it in production. It focuses mainly on Sage 200 Standard (cloud), which uses OAuth 2.0 and has the API enabled by default, with notes included for Sage 200 Professional (on-premise or hosted) where applicable.
Before making any API calls, you need to register your application with Sage to get a Client ID (and Client Secret for web/server applications).
Step 1: Submit the official Sage 200 Client ID and Client Secret Request Form.
Step 2: Sage will process your request (typically within 72 hours) and email you the Client ID and Client Secret (for confidential clients).
Step 3: Store these credentials securely, never expose the Client Secret in client-side code.
✅ At this stage, you have the credentials needed for authentication.
Sage 200 uses OAuth 2.0 Authorization Code Flow with Sage ID for secure, token-based access.
Steps to Implement the Flow:
1. Redirect User to Authorization Endpoint (Ask for Permission):
GET https://id.sage.com/authorize?
audience=s200ukipd/sage200&
client_id={YOUR_CLIENT_ID}&
response_type=code&
redirect_uri={YOUR_REDIRECT_URI}&
scope=openid%20profile%20email%20offline_access&
state={RANDOM_STATE_STRING}2. User logs in with their Sage ID and consents to access.
3. Sage redirects back to your redirect_uri with a code:
{YOUR_REDIRECT_URI}?code={AUTHORIZATION_CODE}&state={YOUR_STATE}4. Exchange Code for Tokens:
POST https://id.sage.com/oauth/token
Content-Type: application/x-www-form-urlencoded
client_id={YOUR_CLIENT_ID}
&client_secret={YOUR_CLIENT_SECRET} // Only for confidential clients
&redirect_uri={YOUR_REDIRECT_URI}
&code={AUTHORIZATION_CODE}
&grant_type=authorization_code5. Refresh Token When Needed:
POST https://id.sage.com/oauth/token
Content-Type: application/x-www-form-urlencoded
client_id={YOUR_CLIENT_ID}
&client_secret={YOUR_CLIENT_SECRET}
&refresh_token={YOUR_REFRESH_TOKEN}
&grant_type=refresh_tokenSage 200 organizes data by sites and companies. You need their IDs for most requests.
Steps:
1. Call the sites endpoint (no X-Site/X-Company headers needed here):
Headers:
Authorization: Bearer {ACCESS_TOKEN}
Content-Type: application/json2. Response lists available sites with site_id, site_name, company_id, etc. Note the ones you need.
Sage 200 API is fully RESTful with OData v4 support for querying.
Key Features:
No SOAP Support in Current API - It's all modern REST/JSON.
All requests require:
Authorization: Bearer {ACCESS_TOKEN}
X-Site: {SITE_ID}
X-Company: {COMPANY_ID}
Content-Type: application/jsonUse Case 1: Fetching Customers (GET)
GET https://api.columbus.sage.com/uk/sage200/accounts/v1/customers?$top=10Response Example (Partial):
[
{
"id": 27828,
"reference": "ABS001",
"name": "ABS Garages Ltd",
"balance": 2464.16,
...
}
]Use Case 2: Creating a Customer (POST)
POST https://api.columbus.sage.com/uk/sage200/accounts/v1/customers
Body:
{
"reference": "NEW001",
"name": "New Customer Ltd",
"short_name": "NEW001",
"credit_limit": 5000.00,
...
}Success: Returns 201 Created with the new customer object.
1. Use Development Credentials from your registration.
2. Test with a demo or non-production site (request via your Sage partner if needed).
3. Tools:
4. Test scenarios: Create/read/update/delete key entities (customers, orders), error handling, token refresh.
5. Monitor responses for errors (e.g., 401 for invalid token).
Building reliable Sage 200 integrations requires understanding platform capabilities and limitations. Following these best practices ensures optimal performance and maintainability.
Sage 200 APIs have practical limits on data volume per request. For large data transfers:
Implement robust error handling:
Ensure data consistency between systems:
Protect sensitive business data:
Choose the right approach for each integration scenario:
Integrating directly with Sage 200 API requires handling complex authentication, data mapping, error handling, and ongoing maintenance. Knit simplifies this by providing a unified integration platform that connects your application to Sage 200 and dozens of other business systems through a single, standardized API.
Instead of writing separate integration code for each ERP system (Sage 200, SAP Business One, Microsoft Dynamics, NetSuite), Knit provides a single Unified ERP API. Your application connects once to Knit and can instantly work with multiple ERP systems without additional development.
Knit automatically handles the differences between systems—different authentication methods, data models, API conventions, and business rules—so you don't have to.
Sage 200 authentication varies by deployment (cloud vs. on-premise) and requires ongoing token management. Knit's pre-built Sage 200 connector handles all authentication complexities:
Your application interacts with a simple, consistent authentication API regardless of the underlying Sage 200 configuration.
Every ERP system has different data models. Sage 200's customer structure differs from SAP's, which differs from NetSuite's. Knit solves this with a Unified Data Model that normalizes data across all supported systems.
When you fetch customers from Sage 200 through Knit, they're automatically transformed into a consistent schema. When you create an order, Knit transforms it from the unified model into Sage 200's specific format. This eliminates the need for custom mapping logic for each integration.
Polling Sage 200 for changes is inefficient and can impact system performance. Knit provides real-time webhooks that notify your application immediately when data changes in Sage 200:
This event-driven approach ensures your application always has the latest data without constant polling.
Building and maintaining a direct Sage 200 integration typically takes months of development and ongoing maintenance. With Knit, you can build a complete integration in days:
Your team can focus on core product functionality instead of integration maintenance.
A. Sage 200 provides API support for both cloud and on-premise versions. The cloud API is generally more feature-rich and follows standard REST/OData patterns. On-premise versions may have limitations based on the specific release.
A. Yes, Sage 200 supports webhooks for certain events, particularly in cloud deployments. You can subscribe to notifications for created, updated, or deleted records. Configuration is done through the Sage 200 administration interface or API. Not all object types support webhooks, so check the specific documentation for your requirements.
A. Sage 200 Cloud enforces API rate limits to ensure system stability:
On-premise deployments may have different limits based on server capacity and configuration. Implement retry logic with exponential backoff to handle rate limit responses gracefully.
A. Yes, Sage provides several options for testing:
A. Sage 200 APIs provide detailed error responses, including:
Enable detailed logging in your integration code and monitor both application logs and Sage 200's audit trails for comprehensive troubleshooting.
A. You can use any programming language that supports HTTP requests and JSON parsing. Sage provides SDKs and examples for:
Community-contributed libraries may be available for other languages. The REST/OData API ensures broad language compatibility.
A. For large data operations:
A. Multiple support channels are available:
.webp)
Jira is one of those tools that quietly powers the backbone of how teams work—whether you're NASA tracking space-bound bugs or a startup shipping sprints on Mondays. Over 300,000 companies use it to keep projects on track, and it’s not hard to see why.
This guide is meant to help you get started with Jira’s API—especially if you’re looking to automate tasks, sync systems, or just make your project workflows smoother. Whether you're exploring an integration for the first time or looking to go deeper with use cases, we’ve tried to keep things simple, practical, and relevant.
At its core, Jira is a powerful tool for tracking issues and managing projects. The Jira API takes that one step further—it opens up everything under the hood so your systems can talk to Jira automatically.
Think of it as giving your app the ability to create tickets, update statuses, pull reports, and tweak workflows—without anyone needing to click around. Whether you're building an integration from scratch or syncing data across tools, the API is how you do it.
It’s well-documented, RESTful, and gives you access to all the key stuff: issues, projects, boards, users, workflows—you name it.
Chances are, your customers are already using Jira to manage bugs, tasks, or product sprints. By integrating with it, you let them:
It’s a win-win. Your users save time by avoiding duplicate work, and your app becomes a more valuable part of their workflow. Plus, once you set up the integration, you open the door to a ton of automation—like auto-updating statuses, triggering alerts, or even creating tasks based on events from your product.
Before you dive into the API calls, it's helpful to understand how Jira is structured. Here are some basics:
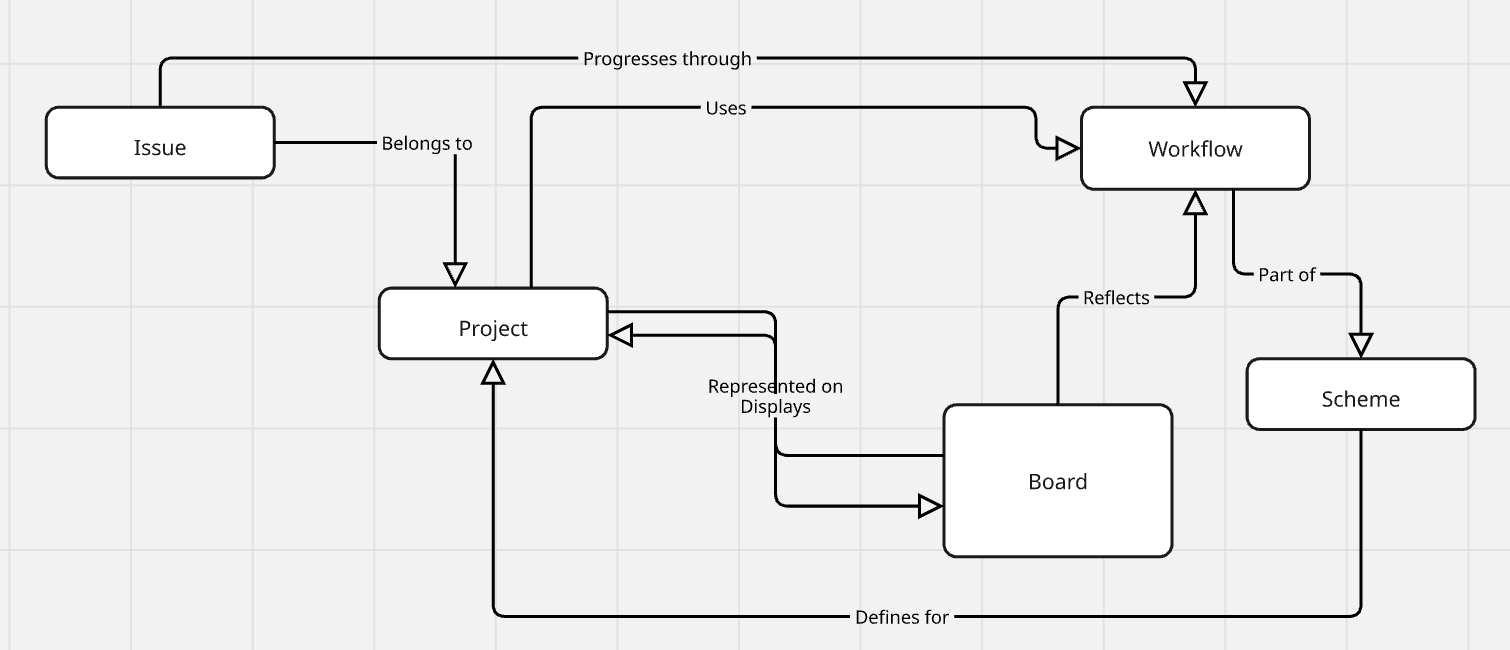
Each of these maps to specific API endpoints. Knowing how they relate helps you design cleaner, more effective integrations.
To start building with the Jira API, here’s what you’ll want to have set up:
If you're using Jira Cloud, you're working with the latest API. If you're on Jira Server/Data Center, there might be a few quirks and legacy differences to account for.
Before you point anything at production, set up a test instance of Jira Cloud. It’s free to try and gives you a safe place to break things while you build.
You can:
Testing in a sandbox means fewer headaches down the line—especially when things go wrong (and they sometimes will).
The official Jira API documentation is your best friend when starting an integration. It's hosted by Atlassian and offers granular details on endpoints, request/response bodies, and error messages. Use the interactive API explorer and bookmark sections such as Authentication, Issues, and Projects to make your development process efficient.
Jira supports several different ways to authenticate API requests. Let’s break them down quickly so you can choose what fits your setup.
Basic authentication is now deprecated but may still be used for legacy systems. It consists of passing a username and password with every request. While easy, it does not have strong security features, hence the phasing out.
OAuth 1.0a has been replaced by more secure protocols. It was previously used for authorization but is now phased out due to security concerns.
For most modern Jira Cloud integrations, API tokens are your best bet. Here’s how you use them:
It’s simple, secure, and works well for most use cases.
If your app needs to access Jira on behalf of users (with their permission), you’ll want to go with 3-legged OAuth. You’ll:
It’s a bit more work upfront, but it gives you scoped, permissioned access.
If you're building apps *inside* the Atlassian ecosystem, you'll either use:
Both offer deeper integrations and more control, but require additional setup.
Whichever method you use, make sure:
A lot of issues during integration come down to misconfigured auth—so double-check before you start debugging the code.
Once you're authenticated, one of the first things you’ll want to do is start interacting with Jira issues. Here’s how to handle the basics: create, read, update, delete (aka CRUD).
To create a new issue, you’ll need to call the `POST /rest/api/3/issue` endpoint with a few required fields:
{
"fields": {
"project": { "key": "PROJ" },
"issuetype": { "name": "Bug" },
"summary": "Something’s broken!",
"description": "Details about the bug go here."
}
}At a minimum, you need the project key, issue type, and summary. The rest—like description, labels, and custom fields—are optional but useful.
Make sure to log the responses so you can debug if anything fails. And yes, retry logic helps if you hit rate limits or flaky network issues.
To fetch an issue, use a GET request:
GET /rest/api/3/issue/{issueIdOrKey}
You’ll get back a JSON object with all the juicy details: summary, description, status, assignee, comments, history, etc.
It’s pretty handy if you’re syncing with another system or building a custom dashboard.
Need to update an issue’s status, add a comment, or change the priority? Use PUT for full updates or PATCH for partial ones.
A common use case is adding a comment:
{
"body": "Following up on this issue—any updates?"
}
Make sure to avoid overwriting fields unintentionally. Always double-check what you're sending in the payload.
Deleting issues is irreversible. Only do it if you're absolutely sure—and always ensure your API token has the right permissions.
It’s best practice to:
Confirm the issue should be deleted (maybe with a soft-delete flag first)
Keep an audit trail somewhere. Handle deletion errors gracefully
Jira comes with a powerful query language called JQL (Jira Query Language) that lets you search for precise issues.
Want all open bugs assigned to a specific user? Or tasks due this week? JQL can help with that.
Example: project = PROJ AND status = "In Progress" AND assignee = currentUser()
When using the search API, don’t forget to paginate: GET /rest/api/3/search?jql=yourQuery&startAt=0&maxResults=50
This helps when you're dealing with hundreds (or thousands) of issues.
The API also allows you to create and manage Jira projects. This is especially useful for automating new customer onboarding.
Use the `POST /rest/api/3/project` endpoint to create a new project, and pass in details like the project key, name, lead, and template.
You can also update project settings and connect them to workflows, issue type schemes, and permission schemes.
If your customers use Jira for agile, you’ll want to work with boards and sprints.
Here’s what you can do with the API:
- Fetch boards (`GET /board`)
- Retrieve or create sprints
- Move issues between sprints
It helps sync sprint timelines or mirror status in an external dashboard.
Jira Workflows define how an issue moves through statuses. You can:
- Get available transitions (`GET /issue/{key}/transitions`)
- Perform a transition (`POST /issue/{key}/transitions`)
This lets you automate common flows like moving an issue to "In Review" after a pull request is merged.
Jira’s API has some nice extras that help you build smarter, more responsive integrations.
You can link related issues (like blockers or duplicates) via the API. Handy for tracking dependencies or duplicate reports across teams.
Example:
{
"type": { "name": "Blocks" },
"inwardIssue": { "key": "PROJ-101" },
"outwardIssue": { "key": "PROJ-102" }
}Always validate the link type you're using and make sure it fits your project config.
Need to upload logs, screenshots, or files? Use the attachments endpoint with a multipart/form-data request.
Just remember:
Want your app to react instantly when something changes in Jira? Webhooks are the way to go.
You can subscribe to events like issue creation, status changes, or comments. When triggered, Jira sends a JSON payload to your endpoint.
Make sure to:
Understanding the differences between Jira Cloud and Jira Server is critical:
Keep updated with the latest changes by monitoring Atlassian’s release notes and documentation.
Even with the best setup, things can (and will) go wrong. Here’s how to prepare for it.
Jira’s API gives back standard HTTP response codes. Some you’ll run into often:
Always log error responses with enough context (request, response body, endpoint) to debug quickly.
Jira Cloud has built-in rate limiting to prevent abuse. It’s not always published in detail, but here’s how to handle it safely:
If you’re building a high-throughput integration, test with realistic volumes and plan for throttling.
To make your integration fast and reliable:
These small tweaks go a long way in keeping your integration snappy and stable.
Getting visibility into your integration is just as important as writing the code. Here's how to keep things observable and testable.
Solid logging = easier debugging. Here's what to keep in mind:
If something breaks, good logs can save hours of head-scratching.
When you’re trying to figure out what’s going wrong:
Also, if your app has logs tied to user sessions or sync jobs, make those searchable by ID.
Testing your Jira integration shouldn’t be an afterthought. It keeps things reliable and easy to update.
The goal is to have confidence in every deploy—not to ship and pray.
Let’s look at a few examples of what’s possible when you put it all together:
Trigger issue creation when a bug or support request is reported:
curl --request POST \
--url 'https://your-domain.atlassian.net/rest/api/3/issue' \
--user 'email@example.com:<api_token>' \
--header 'Accept: application/json' \
--header 'Content-Type: application/json' \
--data '{
"fields": {
"project": { "key": "PROJ" },
"issuetype": { "name": "Bug" },
"summary": "Bug in production",
"description": "A detailed bug report goes here."
}
}'Read issue data from Jira and sync it to another tool:
bash
curl -u email@example.com:API_TOKEN -X GET \ https://your-domain.atlassian.net/rest/api/3/issue/PROJ-123
Map fields like title, status, and priority, and push updates as needed.
Use a scheduled script to move overdue tasks to a "Stuck" column:
```python
import requests
import json
jira_domain = "https://your-domain.atlassian.net"
api_token = "API_TOKEN"
email = "email@example.com"
headers = {"Content-Type": "application/json"}
# Find overdue issues
jql = "project = PROJ AND due < now() AND status != 'Done'"
response = requests.get(f"{jira_domain}/rest/api/3/search",
headers=headers,
auth=(email, api_token),
params={"jql": jql})
for issue in response.json().get("issues", []):
issue_key = issue["key"]
payload = {"transition": {"id": "31"}} # Replace with correct transition ID
requests.post(f"{jira_domain}/rest/api/3/issue/{issue_key}/transitions",
headers=headers,
auth=(email, api_token),
data=json.dumps(payload))
```Automations like this can help keep boards clean and accurate.
Security's key, so let's keep it simple:
Think of API keys like passwords.
Secure secrets = less risk.
If you touch user data:
Quick tips to level up:
Libraries (Java, Python, etc.) can help with the basics.
Your call is based on your needs.
Automate testing and deployment.
Reliable integration = happy you.
If you’ve made it this far—nice work! You’ve got everything you need to build a powerful, reliable Jira integration. Whether you're syncing data, triggering workflows, or pulling reports, the Jira API opens up a ton of possibilities.
Here’s a quick checklist to recap:
Jira is constantly evolving, and so are the use cases around it. If you want to go further:
- Follow [Atlassian’s Developer Changelog]
- Explore the [Jira API Docs]
- Join the [Atlassian Developer Community]
And if you're building on top of Knit, we’re always here to help.
Drop us an email at hello@getknit.dev if you run into a use case that isn’t covered.
Happy building! 🙌
.webp)
Sage Intacct API integration allows businesses to connect financial systems with other applications, enabling real-time data synchronization and reducing errors and missed opportunities. Manual data transfers and outdated processes can lead to errors and missed opportunities. This guide explains how Sage Intacct API integration removes those pain points. We cover the technical setup, common issues, and how using Knit can cut down development time while ensuring a secure connection between your systems and Sage Intacct.
Sage Intacct API integration integrates your financial and ERP systems with third-party applications. It connects your financial information and tools used for reporting, budgeting, and analytics.
The Sage Intacct API documentation provides all the necessary information to integrate your systems with Sage Intacct’s financial services. It covers two main API protocols: REST and SOAP, each designed for different integration needs. REST is commonly used for web-based applications, offering a simple and flexible approach, while SOAP is preferred for more complex and secure transactions.
By following the guidelines, you can ensure a secure and efficient connection between your systems and Sage Intacct.
Integrating Sage Intacct with your existing systems offers a host of advantages.
Before you start the integration process, you should properly set up your environment. Proper setup creates a solid foundation and prevents most pitfalls.
A clear understanding of Sage Intacct’s account types and ecosystem is vital.
A secure environment protects your data and credentials.
Setting up authentication is crucial to secure the data flow.
An understanding of the different APIs and protocols is necessary to choose the best method for your integration needs.
Sage Intacct offers a flexible API ecosystem to fit diverse business needs.
The Sage Intacct REST API offers a clean, modern approach to integrating with Sage Intacct.
Curl request:
curl -i -X GET \ 'https://api.intacct.com/ia/api/v1/objects/cash-management/bank-acount {key}' \-H 'Authorization: Bearer <YOUR_TOKEN_HERE>'Here’s a detailed reference to all the Sage Intacct REST API Endpoints.
For environments that need robust enterprise-level integration, the Sage Intacct SOAP API is a strong option.
Each operation is a simple HTTP request. For example, a GET request to retrieve account details:
Parameters for request body:
<read>
<object>GLACCOUNT</object>
<keys>1</keys>
<fields>*</fields>
</read>Data format for the response body:
Here’s a detailed reference to all the Sage Intacct SOAP API Endpoints.
Comparing SOAP versus REST for various scenarios:
Beyond the primary REST and SOAP APIs, Sage Intacct provides other modules to enhance integration.
Now that your environment is ready and you understand the API options, you can start building your integration.
A basic API call is the foundation of your integration.
Step-by-step guide for a basic API call using REST and SOAP:
REST Example:
Example:
Curl Request:
curl -i -X GET \
https://api.intacct.com/ia/api/v1/objects/accounts-receivable/customer \
-H 'Authorization: Bearer <YOUR_TOKEN_HERE>'
Response 200 (Success):
{
"ia::result": [
{
"key": "68",
"id": "CUST-100",
"href": "/objects/accounts-receivable/customer/68"
},
{
"key": "69",
"id": "CUST-200",
"href": "/objects/accounts-receivable/customer/69"
},
{
"key": "73",
"id": "CUST-300",
"href": "/objects/accounts-receivable/customer/73"
}
],
"ia::meta": {
"totalCount": 3,
"start": 1,
"pageSize": 100
}
}
Response 400 (Failure):
{
"ia::result": {
"ia::error": {
"code": "invalidRequest",
"message": "A POST request requires a payload",
"errorId": "REST-1028",
"additionalInfo": {
"messageId": "IA.REQUEST_REQUIRES_A_PAYLOAD",
"placeholders": {
"OPERATION": "POST"
},
"propertySet": {}
},
"supportId": "Kxi78%7EZuyXBDEGVHD2UmO1phYXDQAAAAo"
}
},
"ia::meta": {
"totalCount": 1,
"totalSuccess": 0,
"totalError": 1
}
}
SOAP Example:
Example snippet of creating a reporting period:
<create>
<REPORTINGPERIOD>
<NAME>Month Ended January 2017</NAME>
<HEADER1>Month Ended</HEADER1>
<HEADER2>January 2017</HEADER2>
<START_DATE>01/01/2017</START_DATE>
<END_DATE>01/31/2017</END_DATE>
<BUDGETING>true</BUDGETING>
<STATUS>active</STATUS>
</REPORTINGPERIOD>
</create>Using Postman for Testing and Debugging API Calls
Postman is a good tool for sending and confirming API requests before implementation to make the testing of your Sage Intacct API integration more efficient.
You can import the Sage Intacct Postman collection into your Postman tool, which has pre-configured endpoints for simple testing. You can use it to simply test your API calls, see results in real time, and debug any issues.
This helps in debugging by visualizing responses and simplifying the identification of errors.
Mapping your business processes to API workflows makes integration smoother.
To test your Sage Intacct API integration, using Postman is recommended. You can import the Sage Intacct Postman collection and quickly make sample API requests to verify functionality. This allows for efficient testing before you begin full implementation.
Understanding real-world applications helps in visualizing the benefits of a well-implemented integration.
This section outlines examples from various sectors that have seen success with Sage Intacct integrations.
Industry
Joining a sage intacct partnership program can offer additional resources and support for your integration efforts.
The partnership program enhances your integration by offering technical and marketing support.
Different partnership tiers cater to varied business needs.
Following best practices ensures that your integration runs smoothly over time.
Manage API calls effectively to handle growth.
Security must remain a top priority.
Effective monitoring helps catch issues early.
No integration is without its challenges. This section covers common problems and how to fix them.
Prepare for and resolve typical issues quickly.
Effective troubleshooting minimizes downtime.
Long-term management of your integration is key to ongoing success.
Stay informed about changes to avoid surprises.
Ensure your integration remains robust as your business grows.
Knit offers a streamlined approach to integrating Sage Intacct. This section details how Knit simplifies the process.
Knit reduces the heavy lifting in integration tasks by offering pre-built accounting connectors in its Unified Accounting API.
This section provides a walk-through for integrating using Knit.
A sample table for mapping objects and fields can be included:
Knit eliminates many of the hassles associated with manual integration.
In this guide, we have walked you through the steps and best practices for integrating Sage Intacct via API. You have learned how to set up a secure environment, choose the right API option, map business processes, and overcome common challenges.
If you're ready to link Sage Intacct with your systems without the need for manual integration, it's time to discover how Knit can assist. Knit delivers customized, secure connectors and a simple interface that shortens development time and keeps maintenance low. Book a demo with Knit today to see firsthand how our solution addresses your integration challenges so you can focus on growing your business rather than worrying about technical roadblocks
.png)
In today's AI-driven world, AI agents have become transformative tools, capable of executing tasks with unparalleled speed, precision, and adaptability. From automating mundane processes to providing hyper-personalized customer experiences, these agents are reshaping the way businesses function and how users engage with technology. However, their true potential lies beyond standalone functionalities—they thrive when integrated seamlessly with diverse systems, data sources, and applications.
This integration is not merely about connectivity; it’s about enabling AI agents to access, process, and act on real-time information across complex environments. Whether pulling data from enterprise CRMs, analyzing unstructured documents, or triggering workflows in third-party platforms, integration equips AI agents to become more context-aware, action-oriented, and capable of delivering measurable value.
This article explores how seamless integrations unlock the full potential of AI agents, the best practices to ensure success, and the challenges that organizations must overcome to achieve seamless and impactful integration.
The rise of Artificial Intelligence (AI) agents marks a transformative shift in how we interact with technology. AI agents are intelligent software entities capable of performing tasks autonomously, mimicking human behavior, and adapting to new scenarios without explicit human intervention. From chatbots resolving customer queries to sophisticated virtual assistants managing complex workflows, these agents are becoming integral across industries.
This rise of use of AI agents has been attributed to factors like:
AI agents are more than just software programs; they are intelligent systems capable of executing tasks autonomously by mimicking human-like reasoning, learning, and adaptability. Their functionality is built on two foundational pillars:
For optimal performance, AI agents require deep contextual understanding. This extends beyond familiarity with a product or service to include insights into customer pain points, historical interactions, and updates in knowledge. However, to equip AI agents with this contextual knowledge, it is important to provide them access to a centralized knowledge base or data lake, often scattered across multiple systems, applications, and formats. This ensures they are working with the most relevant and up-to-date information. Furthermore, they need access to all new information, such as product updates, evolving customer requirements, or changes in business processes, ensuring that their outputs remain relevant and accurate.
For instance, an AI agent assisting a sales team must have access to CRM data, historical conversations, pricing details, and product catalogs to provide actionable insights during a customer interaction.
AI agents’ value lies not only in their ability to comprehend but also to act. For instance, AI agents can perform activities such as updating CRM records after a sales call, generating invoices, or creating tasks in project management tools based on user input or triggers. Similarly, AI agents can initiate complex workflows, such as escalating support tickets, scheduling appointments, or launching marketing campaigns. However, this requires seamless connectivity across different applications to facilitate action.
For example, an AI agent managing customer support could resolve queries by pulling answers from a knowledge base and, if necessary, escalating unresolved issues to a human representative with full context.
The capabilities of AI agents are undeniably remarkable. However, their true potential can only be realized when they seamlessly access contextual knowledge and take informed actions across a wide array of applications. This is where integrations play a pivotal role, serving as the key to bridging gaps and unlocking the full power of AI agents.
The effectiveness of an AI agent is directly tied to its ability to access and utilize data stored across diverse platforms. This is where integrations shine, acting as conduits that connect the AI agent to the wealth of information scattered across different systems. These data sources fall into several broad categories, each contributing uniquely to the agent's capabilities:
Platforms like databases, Customer Relationship Management (CRM) systems (e.g., Salesforce, HubSpot), and Enterprise Resource Planning (ERP) tools house structured data—clean, organized, and easily queryable. For example, CRM integrations allow AI agents to retrieve customer contact details, sales pipelines, and interaction histories, which they can use to personalize customer interactions or automate follow-ups.
The majority of organizational knowledge exists in unstructured formats, such as PDFs, Word documents, emails, and collaborative platforms like Notion or Confluence. Cloud storage systems like Google Drive and Dropbox add another layer of complexity, storing files without predefined schemas. Integrating with these systems allows AI agents to extract key insights from meeting notes, onboarding manuals, or research reports. For instance, an AI assistant integrated with Google Drive could retrieve and summarize a company’s annual performance review stored in a PDF document.
Real-time data streams from IoT devices, analytics tools, or social media platforms offer actionable insights that are constantly updated. AI agents integrated with streaming data sources can monitor metrics, such as energy usage from IoT sensors or engagement rates from Twitter analytics, and make recommendations or trigger actions based on live updates.
APIs from third-party services like payment gateways (Stripe, PayPal), logistics platforms (DHL, FedEx), and HR systems (BambooHR, Workday) expand the agent's ability to act across verticals. For example, an AI agent integrated with a payment gateway could automatically reconcile invoices, track payments, and even issue alerts for overdue accounts.
To process this vast array of data, AI agents rely on data ingestion—the process of collecting, aggregating, and transforming raw data into a usable format. Data ingestion pipelines ensure that the agent has access to a broad and rich understanding of the information landscape, enhancing its ability to make accurate decisions.
However, this capability requires robust integrations with a wide variety of third-party applications. Whether it's CRM systems, analytics tools, or knowledge repositories, each integration provides an additional layer of context that the agent can leverage.
Without these integrations, AI agents would be confined to static or siloed information, limiting their ability to adapt to dynamic environments. For example, an AI-powered customer service bot lacking integration with an order management system might struggle to provide real-time updates on a customer’s order status, resulting in a frustrating user experience.
In many applications, the true value of AI agents lies in their ability to respond with real-time or near-real-time accuracy. Integrations with webhooks and streaming APIs enable the agent to access live data updates, ensuring that its responses remain relevant and timely.
Consider a scenario where an AI-powered invoicing assistant is tasked with generating invoices based on software usage. If the agent relies on a delayed data sync, it might fail to account for a client’s excess usage in the final moments before the invoice is generated. This oversight could result in inaccurate billing, financial discrepancies, and strained customer relationships.
Integrations are not merely a way to access data for AI agents; they are critical to enabling these agents to take meaningful actions on behalf of other applications. This capability is what transforms AI agents from passive data collectors into active participants in business processes.
Integrations play a crucial role in this process by connecting AI agents with different applications, enabling them to interact seamlessly and perform tasks on behalf of the user to trigger responses, updates, or actions in real time.
For instance, A customer service AI agent integrated with CRM platforms can automatically update customer records, initiate follow-up emails, and even generate reports based on the latest customer interactions. SImilarly, if a popular product is running low, the AI agent for e-commerce platform can automatically reorder from the supplier, update the website’s product page with new availability dates, and notify customers about upcoming restocks. Furthermore, A marketing AI agent integrated with CRM and marketing automation platforms (e.g., Mailchimp, ActiveCampaign) can automate email campaigns based on customer behaviors—such as opening specific emails, clicking on links, or making purchases.
Integrations allow AI agents to automate processes that span across different systems. For example, an AI agent integrated with a project management tool and a communication platform can automate task assignments based on project milestones, notify team members of updates, and adjust timelines based on real-time data from work management systems.
For developers driving these integrations, it’s essential to build robust APIs and use standardized protocols like OAuth for secure data access across each of the applications in use. They should also focus on real-time synchronization to ensure the AI agent acts on the most current data available. Proper error handling, logging, and monitoring mechanisms are critical to maintaining reliability and performance across integrations. Furthermore, as AI agents often interact with multiple platforms, developers should design integration solutions that can scale. This involves using scalable data storage solutions, optimizing data flow, and regularly testing integration performance under load.
Retrieval-Augmented Generation (RAG) is a transformative approach that enhances the capabilities of AI agents by addressing a fundamental limitation of generative AI models: reliance on static, pre-trained knowledge. RAG fills this gap by providing a way for AI agents to efficiently access, interpret, and utilize information from a variety of data sources. Here’s how iintegrations help in building RAG pipelines for AI agents:
Traditional APIs are optimized for structured data (like databases, CRMs, and spreadsheets). However, many of the most valuable insights for AI agents come from unstructured data—documents (PDFs), emails, chats, meeting notes, Notion, and more. Unstructured data often contains detailed, nuanced information that is not easily captured in structured formats.
RAG enables AI agents to access and leverage this wealth of unstructured data by integrating it into their decision-making processes. By integrating with these unstructured data sources, AI agents:
RAG involves not only the retrieval of relevant data from these sources but also the generation of responses based on this data. It allows AI agents to pull in information from different platforms, consolidate it, and generate responses that are contextually relevant.
For instance, an HR AI agent might need to pull data from employee records, performance reviews, and onboarding documents to answer a question about benefits. RAG enables this agent to access the necessary context and background information from multiple sources, ensuring the response is accurate and comprehensive through a single retrieval mechanism.
RAG empowers AI agents by providing real-time access to updated information from across various platforms with the help of Webhooks. This is critical for applications like customer service, where responses must be based on the latest data.
For example, if a customer asks about their recent order status, the AI agent can access real-time shipping data from a logistics platform, order history from an e-commerce system, and promotional notes from a marketing database—enabling it to provide a response with the latest information. Without RAG, the agent might only be able to provide a generic answer based on static data, leading to inaccuracies and customer frustration.
While RAG presents immense opportunities to enhance AI capabilities, its implementation comes with a set of challenges. Addressing these challenges is crucial to building efficient, scalable, and reliable AI systems.
Integration of an AI-powered customer service agent with CRM systems, ticketing platforms, and other tools can help enhance contextual knowledge and take proactive actions, delivering a superior customer experience.
For instance, when a customer reaches out with a query—such as a delayed order—the AI agent retrieves their profile from the CRM, including past interactions, order history, and loyalty status, to gain a comprehensive understanding of their background. Simultaneously, it queries the ticketing system to identify any related past or ongoing issues and checks the order management system for real-time updates on the order status. Combining this data, the AI develops a holistic view of the situation and crafts a personalized response. It may empathize with the customer’s frustration, offer an estimated delivery timeline, provide goodwill gestures like loyalty points or discounts, and prioritize the order for expedited delivery.
The AI agent also performs critical backend tasks to maintain consistency across systems. It logs the interaction details in the CRM, updating the customer’s profile with notes on the resolution and any loyalty rewards granted. The ticketing system is updated with a resolution summary, relevant tags, and any necessary escalation details. Simultaneously, the order management system reflects the updated delivery status, and insights from the resolution are fed into the knowledge base to improve responses to similar queries in the future. Furthermore, the AI captures performance metrics, such as resolution times and sentiment analysis, which are pushed into analytics tools for tracking and reporting.
In retail, AI agents can integrate with inventory management systems, customer loyalty platforms, and marketing automation tools for enhancing customer experience and operational efficiency. For instance, when a customer purchases a product online, the AI agent quickly retrieves data from the inventory management system to check stock levels. It can then update the order status in real time, ensuring that the customer is informed about the availability and expected delivery date of the product. If the product is out of stock, the AI agent can suggest alternatives that are similar in features, quality, or price, or provide an estimated restocking date to prevent customer frustration and offer a solution that meets their needs.
Similarly, if a customer frequently purchases similar items, the AI might note this and suggest additional products or promotions related to these interests in future communications. By integrating with marketing automation tools, the AI agent can personalize marketing campaigns, sending targeted emails, SMS messages, or notifications with relevant offers, discounts, or recommendations based on the customer’s previous interactions and buying behaviors. The AI agent also writes back data to customer profiles within the CRM system. It logs details such as purchase history, preferences, and behavioral insights, allowing retailers to gain a deeper understanding of their customers’ shopping patterns and preferences.
Integrating AI (Artificial Intelligence) and RAG (Recommendations, Actions, and Goals) frameworks into existing systems is crucial for leveraging their full potential, but it introduces significant technical challenges that organizations must navigate. These challenges span across data ingestion, system compatibility, and scalability, often requiring specialized technical solutions and ongoing management to ensure successful implementation.
Adding integrations to AI agents involves providing these agents with the ability to seamlessly connect with external systems, APIs, or services, allowing them to access, exchange, and act on data. Here are the top ways to achieve the same:
Custom development involves creating tailored integrations from scratch to connect the AI agent with various external systems. This method requires in-depth knowledge of APIs, data models, and custom logic. The process involves developing specific integrations to meet unique business requirements, ensuring complete control over data flows, transformations, and error handling. This approach is suitable for complex use cases where pre-built solutions may not suffice.
Embedded iPaaS (Integration Platform as a Service) solutions offer pre-built integration platforms that include no-code or low-code tools. These platforms allow organizations to quickly and easily set up integrations between the AI agent and various external systems without needing deep technical expertise. The integration process is simplified by using a graphical interface to configure workflows and data mappings, reducing development time and resource requirements.
Unified API solutions provide a single API endpoint that connects to multiple SaaS products and external systems, simplifying the integration process. This method abstracts the complexity of dealing with multiple APIs by consolidating them into a unified interface. It allows the AI agent to access a wide range of services, such as CRM systems, marketing platforms, and data analytics tools, through a seamless and standardized integration process.
Knit offers a game-changing solution for organizations looking to integrate their AI agents with a wide variety of SaaS applications quickly and efficiently. By providing a seamless, AI-driven integration process, Knit empowers businesses to unlock the full potential of their AI agents by connecting them with the necessary tools and data sources.
By integrating with Knit, organizations can power their AI agents to interact seamlessly with a wide array of applications. This capability not only enhances productivity and operational efficiency but also allows for the creation of innovative use cases that would be difficult to achieve with manual integration processes. Knit thus transforms how businesses utilize AI agents, making it easier to harness the full power of their data across multiple platforms.
Ready to see how Knit can transform your AI agents? Contact us today for a personalized demo!
.png)
In today’s fast-paced digital landscape, organizations across all industries are leveraging Calendar APIs to streamline scheduling, automate workflows, and optimize resource management. While standalone calendar applications have always been essential, Calendar Integration significantly amplifies their value—making it possible to synchronize events, reminders, and tasks across multiple platforms seamlessly. Whether you’re a SaaS provider integrating a customer’s calendar or an enterprise automating internal processes, a robust API Calendar strategy can drastically enhance efficiency and user satisfaction.
Explore more Calendar API integrations
In this comprehensive guide, we’ll discuss the benefits of Calendar API integration, best practices for developers, real-world use cases, and tips for managing common challenges like time zone discrepancies and data normalization. By the end, you’ll have a clear roadmap on how to build and maintain effective Calendar APIs for your organization or product offering in 2025.
In 2025, calendars have evolved beyond simple day-planners to become strategic tools that connect individuals, teams, and entire organizations. The real power comes from Calendar Integration, or the ability to synchronize these planning tools with other critical systems—CRM software, HRIS platforms, applicant tracking systems (ATS), eSignature solutions, and more.
Essentially, Calendar API integration becomes indispensable for any software looking to reduce operational overhead, improve user satisfaction, and scale globally.
One of the most notable advantages of Calendar Integration is automated scheduling. Instead of manually entering data into multiple calendars, an API can do it for you. For instance, an event management platform integrating with Google Calendar or Microsoft Outlook can immediately update participants’ schedules once an event is booked. This eliminates the need for separate email confirmations and reduces human error.
When a user can book or reschedule an appointment without back-and-forth emails, you’ve substantially upgraded their experience. For example, healthcare providers that leverage Calendar APIs can let patients pick available slots and sync these appointments directly to both the patient’s and the doctor’s calendars. Changes on either side trigger instant notifications, drastically simplifying patient-doctor communication.
By aligning calendars with HR systems, CRM tools, and project management platforms, businesses can ensure every resource—personnel, rooms, or equipment—is allocated efficiently. Calendar-based resource mapping can reduce double-bookings and idle times, increasing productivity while minimizing conflicts.
Notifications are integral to preventing missed meetings and last-minute confusion. Whether you run a field service company, a professional consulting firm, or a sales organization, instant schedule updates via Calendar APIs keep everyone on the same page—literally.
API Calendar solutions enable triggers and actions across diverse systems. For instance, when a sales lead in your CRM hits “hot” status, the system can automatically schedule a follow-up call, add it to the rep’s calendar, and send a reminder 15 minutes before the meeting. Such automation fosters a frictionless user experience and supports consistent follow-ups.
<a name="calendar-api-data-models-explained"></a>
To integrate calendar functionalities successfully, a solid grasp of the underlying data structures is crucial. While each calendar provider may have specific fields, the broad data model often consists of the following objects:
Properly mapping these objects during Calendar Integration ensures consistent data handling across multiple systems. Handling each element correctly—particularly with recurring events—lays the foundation for a smooth user experience.
Below are several well-known Calendar APIs that dominate the market. Each has unique features, so choose based on your users’ needs:
Applicant Tracking Systems (ATS) like Lever or Greenhouse can integrate with Google Calendar or Outlook to automate interview scheduling. Once a candidate is selected for an interview, the ATS checks availability for both the interviewer and candidate, auto-generates an event, and sends reminders. This reduces manual coordination, preventing double-bookings and ensuring a smooth interview process.
Learn more on How Interview Scheduling Companies Can Scale ATS Integrations Faster
ERPs like SAP or Oracle NetSuite handle complex scheduling needs for workforce or equipment management. By integrating with each user’s calendar, the ERP can dynamically allocate resources based on real-time availability and location, significantly reducing conflicts and idle times.
Salesforce and HubSpot CRMs can automatically book demos and follow-up calls. Once a customer selects a time slot, the CRM updates the rep’s calendar, triggers reminders, and logs the meeting details—keeping the sales cycle organized and on track.
Systems like Workday and BambooHR use Calendar APIs to automate onboarding schedules—adding orientation, training sessions, and check-ins to a new hire’s calendar. Managers can see progress in real-time, ensuring a structured, transparent onboarding experience.
Assessment tools like HackerRank or Codility integrate with Calendar APIs to plan coding tests. Once a test is scheduled, both candidates and recruiters receive real-time updates. After completion, debrief meetings are auto-booked based on availability.
DocuSign or Adobe Sign can create calendar reminders for upcoming document deadlines. If multiple signatures are required, it schedules follow-up reminders, ensuring legal or financial processes move along without hiccups.
QuickBooks or Xero integrations place invoice due dates and tax deadlines directly onto the user’s calendar, complete with reminders. Users avoid late penalties and maintain financial compliance with minimal manual effort.
While Calendar Integration can transform workflows, it’s not without its hurdles. Here are the most prevalent obstacles:
Businesses can integrate Calendar APIs either by building direct connectors for each calendar platform or opting for a Unified Calendar API provider that consolidates all integrations behind a single endpoint. Here’s how they compare:
Learn more about what should you look for in a Unified API Platform
The calendar landscape is only getting more complex as businesses and end users embrace an ever-growing range of tools and platforms. Implementing an effective Calendar API strategy—whether through direct connectors or a unified platform—can yield substantial operational efficiencies, improved user satisfaction, and a significant competitive edge. From Calendar APIs that power real-time notifications to AI-driven features predicting best meeting times, the potential for innovation is limitless.
If you’re looking to add API Calendar capabilities to your product or optimize an existing integration, now is the time to take action. Start by assessing your users’ needs, identifying top calendar providers they rely on, and determining whether a unified or direct connector strategy makes the most sense. Incorporate the best practices highlighted in this guide—like leveraging webhooks, managing data normalization, and handling rate limits—and you’ll be well on your way to delivering a next-level calendar experience.
Ready to transform your Calendar Integration journey?
Book a Demo with Knit to See How AI-Driven Unified APIs Simplify Integrations
By following the strategies in this comprehensive guide, you’ll not only harness the power of Calendar APIs but also future-proof your software or enterprise operations for the decade ahead. Whether you’re automating interviews, scheduling field services, or synchronizing resources across continents, Calendar Integration is the key to eliminating complexity and turning time management into a strategic asset.
.webp)
This guide is part of our growing collection on HRIS integrations. We’re continuously exploring new apps and updating our HRIS Guides Directory with fresh insights.
Workday has become one of the most trusted platforms for enterprise HR, payroll, and financial management. It’s the system of record for employee data in thousands of organizations. But as powerful as Workday is, most businesses don’t run only on Workday. They also use performance management tools, applicant tracking systems, payroll software, CRMs, SaaS platforms, and more.
The challenge? Making all these systems talk to each other.
That’s where the Workday API comes in. By integrating with Workday’s APIs, companies can automate processes, reduce manual work, and ensure accurate, real-time data flows between systems.
In this blog, we’ll give you everything you need, whether you’re a beginner just learning about APIs or a developer looking to build an enterprise-grade integration.
We’ll cover terminology, use cases, step-by-step setup, code examples, and FAQs. By the end, you’ll know how Workday API integration works and how to do it the right way.
Looking to quickstart with the Workday API Integration? Check our Workday API Directory for common Workday API endpoints
Workday integrations can support both internal workflows for your HR and finance teams, as well as customer-facing use cases that make SaaS products more valuable. Let’s break down some of the most impactful examples.
Performance reviews are key to fair salary adjustments, promotions, and bonus payouts. Many organizations use tools like Lattice to manage reviews and feedback, but without accurate employee data, the process can become messy.
By integrating Lattice with Workday, job titles and salaries stay synced and up to date. HR teams can run performance cycles with confidence, and once reviews are done, compensation changes flow back into Workday automatically — keeping both systems aligned and reducing manual work.
Onboarding new employees is often a race against time , from getting payroll details set up to preparing IT access. With Workday, you can automate this process.
For example, by integrating an ATS like Greenhouse with Workday:
For SaaS companies, onboarding users efficiently is key to customer satisfaction. Workday integrations make this scalable.
Take BILL, a financial operations platform, as an example:
Offboarding is just as important as onboarding, especially for maintaining security. If a terminated employee retains access to systems, it creates serious risks.
Platforms like Ramp, a spend management solution, solve this through Workday integrations:
While this guide equips developers with the skills to build robust Workday integrations through clear explanations and practical examples, the benefits extend beyond the development team. You can also expand your HRIS integrations with the Workday API integration and automate tedious tasks like data entry, freeing up valuable time to focus on other important work. Business leaders gain access to real-time insights across their entire organization, empowering them to make data-driven decisions that drive growth and profitability. This guide empowers developers to build integrations that streamline HR workflows, unlock real-time data for leaders, and ultimately unlock Workday's full potential for your organization.
Understanding key terms is essential for effective integration with Workday. Let’s look upon few of them, that will be frequently used ahead -
1. API Types: Workday offers REST and SOAP APIs, which serve different purposes. REST APIs are commonly used for web-based integrations, while SOAP APIs are often utilized for complex transactions.
2. Endpoint Structure: You must familiarize yourself with the Workday API structure as each endpoint corresponds to a specific function. A common workday API example would be retrieving employee data or updating payroll information.
3. API Documentation: Workday API documentation provides a comprehensive overview of both REST and SOAP APIs.
Workday supports two primary ways to authenticate API calls. Which one you use depends on the API family you choose:
SOAP requests are authenticated with a special Workday user account (the ISU) using WS-Security headers. Access is controlled by the security group(s) and domain policies assigned to that ISU.
REST requests use OAuth 2.0. You register an API client in Workday, grant scopes (what the client is allowed to access), and obtain access tokens (and a refresh token) to call endpoints.
To ensure a secure and reliable connection with Workday's APIs, this section outlines the essential prerequisites. These steps will lay the groundwork for a successful integration, enabling seamless data exchange and unlocking the full potential of Workday within your existing technological infrastructure.
Now that you have a comprehensive overview of the steps required to build a Workday API Integration and an overview of the Workday API documentation, lets dive deep into each step so you can build your Workday integration confidently!
The Web Services Endpoint for the Workday tenant serves as the gateway for integrating external systems with Workday's APIs, enabling data exchange and communication between platforms. To access your specific Workday web services endpoint, follow these steps:
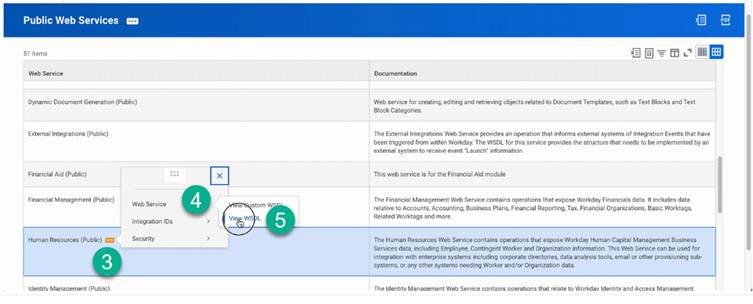
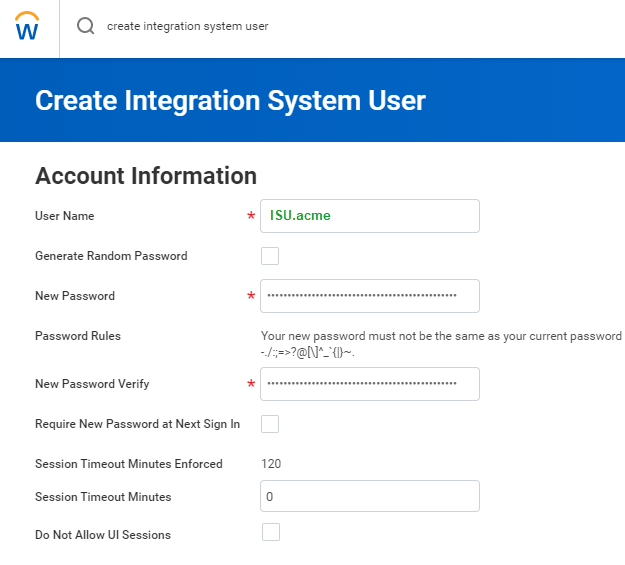
Next, you need to establish an Integration System User (ISU) in Workday, dedicated to managing API requests. This ensures enhanced security and enables better tracking of integration actions. Follow the below steps to set up an ISU in Workday:
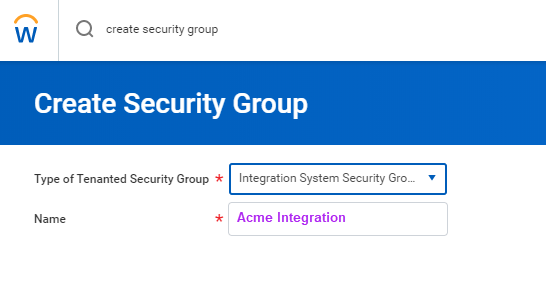
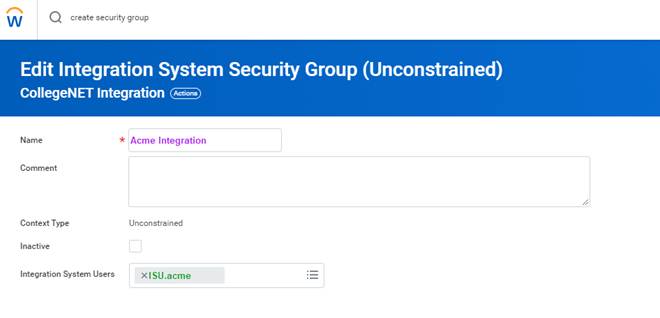
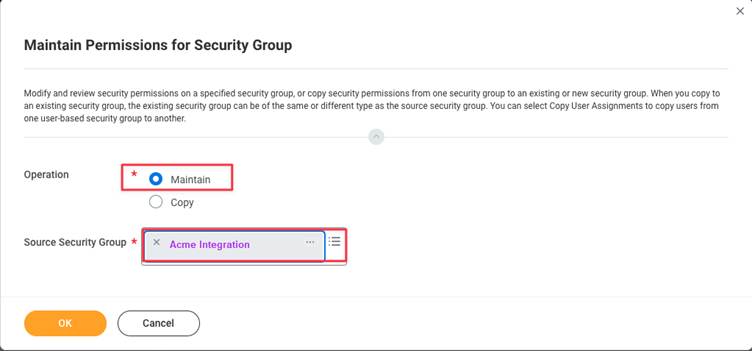

Note: The permissions listed below are necessary for the full HRIS API. These permissions may vary depending on the specific implementation
Parent Domains for HRIS
Parent Domains for HRIS
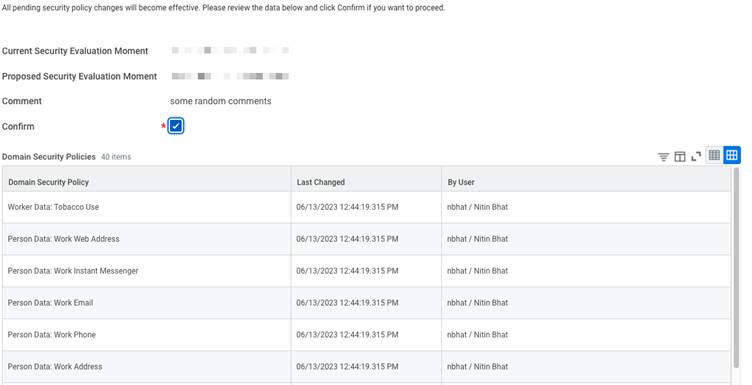
Workday offers different authentication methods. Here, we will focus on OAuth 2.0, a secure way for applications to gain access through an ISU (Integrated System User). An ISU acts like a dedicated user account for your integration, eliminating the need to share individual user credentials. Below steps highlight how to obtain OAuth 2.0 tokens in Workday:
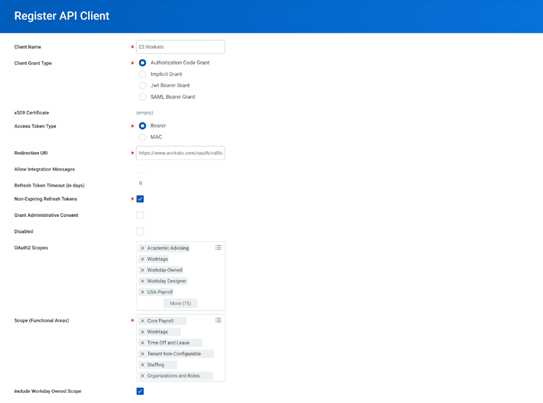
When building a Workday integration, one of the first decisions you’ll face is: Should I use SOAP or REST?
Both are supported by Workday, but they serve slightly different purposes. Let’s break it down.
SOAP (Simple Object Access Protocol) has been around for years and is still widely used in Workday, especially for sensitive data and complex transactions.
How to work with SOAP:
REST (Representational State Transfer) is the newer, lighter, and easier option for Workday integrations. It’s widely used in SaaS products and web apps.
Advantages of REST APIs
How to work with REST:
Now that you have picked between SOAP and REST, let's proceed to utilize Workday HCM APIs effectively. We'll walk through creating a new employee and fetching a list of all employees – essential building blocks for your integration. Remember, if you are using SOAP, you will authenticate your requests with an ISU user name and password, while if your are using REST, you will authenticate your requests with access tokens generated by using the OAuth refresh tokens we generated in the above steps.
In this guide, we will focus on using SOAP to construct our API requests.
First let's learn about constructing a SOAP Request Body
SOAP requests follow a specific format and use XML to structure the data. Here's an example of a SOAP request body to fetch employees using the Get Workers endpoint:
<soapenv:Envelope
xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:bsvc="urn:com.workday/bsvc">
<soapenv:Header>
<wsse:Security>
<wsse:UsernameToken>
<wsse:Username>{ISU USERNAME}</wsse:Username>
<wsse:Password>{ISU PASSWORD}</wsse:Password>
</wsse:UsernameToken>
</wsse:Security>
</soapenv:Header>
<soapenv:Body>
<bsvc:Get_Workers_Request xmlns:bsvc="urn:com.workday/bsvc" bsvc:version="v40.1">
</bsvc:Get_Workers_Request>
</soapenv:Body>
</soapenv:Envelope>👉 How it works:
Now that you know how to construct a SOAP request, let's look at a couple of real life Workday integration use cases:
Let's add a new team member. For this we will use the Hire Employee API! It lets you send employee details like name, job title, and salary to Workday. Here's a breakdown:
curl --location 'https://wd2-impl-services1.workday.com/ccx/service/{TENANT}/Staffing/v42.0' \
--header 'Content-Type: application/xml' \
--data-raw '<soapenv:Envelope xmlns:bsvc="urn:com.workday/bsvc" xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
<soapenv:Header>
<wsse:Security>
<wsse:UsernameToken>
<wsse:Username>{ISU_USERNAME}</wsse:Username>
<wsse:Password>{ISU_PASSWORD}</wsse:Password>
</wsse:UsernameToken>
</wsse:Security>
<bsvc:Workday_Common_Header>
<bsvc:Include_Reference_Descriptors_In_Response>true</bsvc:Include_Reference_Descriptors_In_Response>
</bsvc:Workday_Common_Header>
</soapenv:Header>
<soapenv:Body>
<bsvc:Hire_Employee_Request bsvc:version="v42.0">
<bsvc:Business_Process_Parameters>
<bsvc:Auto_Complete>true</bsvc:Auto_Complete>
<bsvc:Run_Now>true</bsvc:Run_Now>
</bsvc:Business_Process_Parameters>
<bsvc:Hire_Employee_Data>
<bsvc:Applicant_Data>
<bsvc:Personal_Data>
<bsvc:Name_Data>
<bsvc:Legal_Name_Data>
<bsvc:Name_Detail_Data>
<bsvc:Country_Reference>
<bsvc:ID bsvc:type="ISO_3166-1_Alpha-3_Code">USA</bsvc:ID>
</bsvc:Country_Reference>
<bsvc:First_Name>Employee</bsvc:First_Name>
<bsvc:Last_Name>New</bsvc:Last_Name>
</bsvc:Name_Detail_Data>
</bsvc:Legal_Name_Data>
</bsvc:Name_Data>
<bsvc:Contact_Data>
<bsvc:Email_Address_Data bsvc:Delete="false" bsvc:Do_Not_Replace_All="true">
<bsvc:Email_Address>employee@work.com</bsvc:Email_Address>
<bsvc:Usage_Data bsvc:Public="true">
<bsvc:Type_Data bsvc:Primary="true">
<bsvc:Type_Reference>
<bsvc:ID bsvc:type="Communication_Usage_Type_ID">WORK</bsvc:ID>
</bsvc:Type_Reference>
</bsvc:Type_Data>
</bsvc:Usage_Data>
</bsvc:Email_Address_Data>
</bsvc:Contact_Data>
</bsvc:Personal_Data>
</bsvc:Applicant_Data>
<bsvc:Position_Reference>
<bsvc:ID bsvc:type="Position_ID">P-SDE</bsvc:ID>
</bsvc:Position_Reference>
<bsvc:Hire_Date>2024-04-27Z</bsvc:Hire_Date>
</bsvc:Hire_Employee_Data>
</bsvc:Hire_Employee_Request>
</soapenv:Body>
</soapenv:Envelope>'Elaboration:
Response:
<bsvc:Hire_Employee_Event_Response
xmlns:bsvc="urn:com.workday/bsvc" bsvc:version="string">
<bsvc:Employee_Reference bsvc:Descriptor="string">
<bsvc:ID bsvc:type="ID">EMP123</bsvc:ID>
</bsvc:Employee_Reference>
</bsvc:Hire_Employee_Event_Response>If everything goes well, you'll get a success message and the ID of the newly created employee!
Now, if you want to grab a list of all your existing employees. The Get Workers API is your friend!
Below is workday API get workers example:
curl --location 'https://wd2-impl-services1.workday.com/ccx/service/{TENANT}/Human_Resources/v40.1' \
--header 'Content-Type: application/xml' \
--data '<soapenv:Envelope
xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:bsvc="urn:com.workday/bsvc">
<soapenv:Header>
<wsse:Security>
<wsse:UsernameToken>
<wsse:Username>{ISU_USERNAME}</wsse:Username>
<wsse:Password>{ISU_USERNAME}</wsse:Password>
</wsse:UsernameToken>
</wsse:Security>
</soapenv:Header>
<soapenv:Body>
<bsvc:Get_Workers_Request xmlns:bsvc="urn:com.workday/bsvc" bsvc:version="v40.1">
<bsvc:Response_Filter>
<bsvc:Count>10</bsvc:Count>
<bsvc:Page>1</bsvc:Page>
</bsvc:Response_Filter>
<bsvc:Response_Group>
<bsvc:Include_Reference>true</bsvc:Include_Reference>
<bsvc:Include_Personal_Information>true</bsvc:Include_Personal_Information>
</bsvc:Response_Group>
</bsvc:Get_Workers_Request>
</soapenv:Body>
</soapenv:Envelope>'This is a simple GET request to the Get Workers endpoint.
Elaboration:
Response:
<?xml version='1.0' encoding='UTF-8'?>
<env:Envelope xmlns:env="http://schemas.xmlsoap.org/soap/envelope/">
<env:Body>
<wd:Get_Workers_Response xmlns:wd="urn:com.workday/bsvc" wd:version="v40.1">
<wd:Response_Filter>
<wd:Page>1</wd:Page>
<wd:Count>1</wd:Count>
</wd:Response_Filter>
<wd:Response_Data>
<wd:Worker>
<wd:Worker_Data>
<wd:Worker_ID>21001</wd:Worker_ID>
<wd:User_ID>lmcneil</wd:User_ID>
<wd:Personal_Data>
<wd:Name_Data>
<wd:Legal_Name_Data>
<wd:Name_Detail_Data wd:Formatted_Name="Logan McNeil" wd:Reporting_Name="McNeil, Logan">
<wd:Country_Reference>
<wd:ID wd:type="WID">bc33aa3152ec42d4995f4791a106ed09</wd:ID>
<wd:ID wd:type="ISO_3166-1_Alpha-2_Code">US</wd:ID>
<wd:ID wd:type="ISO_3166-1_Alpha-3_Code">USA</wd:ID>
<wd:ID wd:type="ISO_3166-1_Numeric-3_Code">840</wd:ID>
</wd:Country_Reference>
<wd:First_Name>Logan</wd:First_Name>
<wd:Last_Name>McNeil</wd:Last_Name>
</wd:Name_Detail_Data>
</wd:Legal_Name_Data>
</wd:Name_Data>
<wd:Contact_Data>
<wd:Address_Data wd:Effective_Date="2008-03-25" wd:Address_Format_Type="Basic" wd:Formatted_Address="42 Laurel Street&#xa;San Francisco, CA 94118&#xa;United States of America" wd:Defaulted_Business_Site_Address="0">
</wd:Address_Data>
<wd:Phone_Data wd:Area_Code="415" wd:Phone_Number_Without_Area_Code="441-7842" wd:E164_Formatted_Phone="+14154417842" wd:Workday_Traditional_Formatted_Phone="+1 (415) 441-7842" wd:National_Formatted_Phone="(415) 441-7842" wd:International_Formatted_Phone="+1 415-441-7842" wd:Tenant_Formatted_Phone="+1 (415) 441-7842">
</wd:Phone_Data>
</wd:Worker_Data>
</wd:Worker>
</wd:Response_Data>
</wd:Get_Workers_Response>
</env:Body>
</env:Envelope>This JSON array gives you details of all your employees including details like the name, email, phone number and more.
Use a tool like Postman or curl to POST this XML to your Workday endpoint.
If you used REST instead, the same “Get Workers” request would look much simpler:
curl --location 'https://{host}.workday.com/ccx/api/v1/{tenant}/workers' \
--header 'Authorization: Bearer {ACCESS_TOKEN}'Before moving your integration to production, it’s always safer to test everything in a sandbox environment. A sandbox is like a practice environment; it contains test data and behaves like production but without the risk of breaking live systems.
Here’s how to use a sandbox effectively:
Ask your Workday admin to provide you with a sandbox environment. Specify the type of sandbox you need (development, test, or preview). If you are a Knit customer on the Scale or Enterprise plan, Knit will provide you access to a Workday sandbox for integration testing.
Log in to your sandbox and configure it so it looks like your production environment. Add sample company data, roles, and permissions that match your real setup.
Just like in production, create a dedicated ISU account in the sandbox. Assign it the necessary permissions to access the required APIs.
Register your application inside the sandbox to get client credentials (Client ID & Secret). These credentials will be used for secure API calls in your test environment.
Use tools like Postman or cURL to send test requests to the sandbox. Test different scenarios (e.g., creating a worker, fetching employees, updating job info). Identify and fix errors before deploying to production.
Use Workday’s built-in logs to track API requests and responses. Look for failures, permission issues, or incorrect payloads. Fix issues in your code or configuration until everything runs smoothly.
Once your integration has been thoroughly tested in the sandbox and you’re confident that everything works smoothly, the next step is moving it to the production environment. To do this, you need to replace all sandbox details with production values. This means updating the URLs to point to your production Workday tenant and switching the ISU (Integration System User) credentials to the ones created for production use.
When your integration is live, it’s important to make sure you can track and troubleshoot it easily. Setting up detailed logging will help you capture every API request and response, making it much simpler to identify and fix issues when they occur. Alongside logging, monitoring plays a key role. By keeping track of performance metrics such as response times and error rates, you can ensure the integration continues to run smoothly and catch problems before they affect your workflows.
If you’re using Knit, you also get the advantage of built-in observability dashboards. These dashboards give you real-time visibility into your live integration, making debugging and ongoing maintenance far easier. With the right preparation and monitoring in place, moving from sandbox to production becomes a smooth and reliable process.
PECI (Payroll Effective Change Interface) lets you transmit employee data changes (like new hires, raises, or terminations) directly to your payroll provider, slashing manual work and errors. Below you will find a brief comparison of PECI and Web Services and also the steps required to setup PECI in Workday
Feature: PECI
Feature: Web Services
PECI set up steps :-
Workday does not natively support real-time webhooks. This means you can’t automatically get notified whenever an event happens in Workday (like a new employee being hired or someone’s role being updated). Instead, most integrations rely on polling, where your system repeatedly checks Workday for updates. While this works, it can be inefficient and slow compared to event-driven updates.
This is exactly where Knit Virtual Webhooks step in. Knit simulates webhook functionality for systems like Workday that don’t offer it out of the box.
Knit continuously monitors changes in Workday (such as employee updates, terminations, or payroll changes). When a change is detected, it instantly triggers a virtual webhook event to your application. This gives you real-time updates without having to build complex polling logic.
For example: If a new hire is added in Workday, Knit can send a webhook event to your product immediately, allowing you to provision access or update records in real time — just like native webhooks.
Getting stuck with errors can be frustrating and time-consuming. Although many times we face errors that someone else has already faced, and to avoid giving in hours to handle such errors, we have put some common errors below and solutions to how you can handle them.
Integrating with Workday can unlock huge value for your business, but it also comes with challenges. Here are some important best practices to keep in mind as you build and maintain your integration.
Workday supports two main authentication methods: ISU (Integration System User) and OAuth 2.0. The choice between them depends on your security needs and integration goals.
If your integration is customer-facing, don’t just focus on building it , think about how you’ll launch it. A Workday integration can be a major selling point, and many customers will expect it.
Before going live, align on:
This ensures your team is ready to deliver value from day one and can even help close deals faster.
Building and maintaining a Workday integration completely in-house can be very time-consuming. Your developers may spend months just scoping, coding, and testing the integration. And once it’s live, maintenance can become a headache.
For example, even a small change , like Workday returning a value in a different format (string instead of number) , could break your integration. Keeping up with these edge cases pulls your engineers away from core product work.
A third-party integration platform like Knit can solve this problem. These platforms handle the heavy lifting , scoping, development, testing, and maintenance , while also giving you features like observability dashboards, virtual webhooks, and broader HRIS coverage. This saves engineering time, speeds up your launch, and ensures your integration stays reliable over time.
We know you're here to conquer Workday integrations, and at Knit (rated #1 for ease of use as of 2025!), we're here to help! Knit offers a unified API platform which lets you connect your application to multiple HRIS, CRM, Accounting, Payroll, ATS, ERP, and more tools in one go.
Advantages of Knit for Workday Integrations
Getting Started with Knit
REST Unified API Approach with Knit
A Workday integration is a connection built between Workday and another system (like payroll, CRM, or ATS) that allows data to flow seamlessly between them. These integrations can be created using APIs, files (CSV/XML), databases, or scripts , depending on the use case and system design.
A Workday API integration is a type of integration where you use Workday’s APIs (SOAP or REST) to connect Workday with other applications. This lets you securely access, read, and update Workday data in real time.
It depends on your approach.
Workday offers:
Workday doesn’t publish all rate limits publicly. Most details are available only to customers or partners. However, some endpoints have documented limits , for example, the Strategic Sourcing Projects API allows up to 5 requests per second. Always design your integration with pagination, retry logic, and throttling to avoid issues.
Workday provides sandbox environments to its customers for development and testing. If you’re a software vendor (not a Workday customer), you typically need a partnership agreement with Workday to get access. Some third-party platforms like Knit also provide sandbox access for integration testing.
Workday supports two main methods:
Yes. Workday provides both SOAP and REST APIs, covering a wide range of data domains, HR, recruiting, payroll, compensation, time tracking, and more. REST APIs are typically preferred because they are easier to implement, faster, and more developer-friendly.
Yes. If you are a Workday customer or have a formal partnership, you can build integrations with their APIs. Without access, you won’t be able to authenticate or use Workday’s endpoints.
No, Workday does not natively support webhooks. However, you can use polling (fetching data periodically) or platforms like Knit, which provide virtual webhooks to simulate real-time updates.
A custom Workday integration can take weeks or even months, depending on complexity. Using a unified API platform can cut this down to days by providing pre-built connectors and standardized endpoints.
Resources to get you started on your integrations journey
Learn how to build your specific integrations use case with Knit
-p-1080.png)
In today's fast-evolving business landscape, companies are streamlining employee financial offerings, particularly in payroll-linked payments and leasing solutions. These include auto-leasing programs, payroll-based financing, and other benefits designed to enhance employee financial well-being.
By integrating directly with an organization’s Human Resources Information System (HRIS) and payroll systems, solution providers can offer a seamless experience that benefits both employers (B2B) and employees (B2C). This guide explores the importance of payroll integration, challenges businesses face, and best practices for implementing scalable solutions, with insights drawn from the B2B auto-leasing sector.
Payroll-linked leasing and financing offer key advantages for companies and employees:
Despite its advantages, integrating payroll-based solutions presents several challenges:
Integrating payroll systems into leasing platforms enables:
A structured payroll integration process typically follows these steps:
To ensure a smooth and efficient integration, follow these best practices:
A robust payroll integration system must address:
A high-level architecture for payroll integration includes:
┌────────────────┐ ┌─────────────────┐
│ HR System │ │ Payroll │
│(Cloud/On-Prem) │ → │(Deduction Logic)│
└───────────────┘ └─────────────────┘
│ (API/Connector)
▼
┌──────────────────────────────────────────┐
│ Unified API Layer │
│ (Manages employee data & payroll flow) │
└──────────────────────────────────────────┘
│ (Secure API Integration)
▼
┌───────────────────────────────────────────┐
│ Leasing/Finance Application Layer │
│ (Approvals, User Portal, Compliance) │
└───────────────────────────────────────────┘
A single API integration that connects various HR systems enables scalability and flexibility. Solutions like Knit offer pre-built integrations with 40+ HRMS and payroll systems, reducing complexity and development costs.
To implement payroll-integrated leasing successfully, follow these steps:
Payroll-integrated leasing solutions provide significant advantages for employers and employees but require well-planned, secure integrations. By leveraging a unified API layer, automating approval workflows, and payroll deductions data, businesses can streamline operations while enhancing employee financial wellness.
For companies looking to reduce overhead and accelerate implementation, adopting a pre-built API solution can simplify payroll integration while allowing them to focus on their core leasing offerings. Now is the time to map out your integration strategy, define your data requirements, and build a scalable solution that transforms the employee leasing experience.
Ready to implement a seamless payroll-integrated leasing solution? Take the next step today by exploring unified API platforms and optimizing your HR-tech stack for maximum efficiency. To talk to our solutions experts at Knit you can reach out to us here

Seamless CRM and ticketing system integrations are critical for modern customer support software. However, developing and maintaining these integrations in-house is time-consuming and resource-intensive.
In this article, we explore how Knit’s Unified API simplifies customer support integrations, enabling teams to connect with multiple platforms—HubSpot, Zendesk, Intercom, Freshdesk, and more—through a single API.
Customer support platforms depend on real-time data exchange with CRMs and ticketing systems. Without seamless integrations:
A unified API solution eliminates these issues, accelerating integration processes and reducing ongoing maintenance burdens.
Developing custom integrations comes with key challenges:
For example a company offering video-assisted customer support where users can record and send videos along with support tickets. Their integration requirements include:
With Knit’s Unified API, these steps become significantly simpler.
By leveraging Knit’s single API interface, companies can automate workflows and reduce development time. Here’s how:
Knit provides pre-built ticketing APIs to simplify integration with customer support systems:
For a successful integration, follow these best practices:
Streamline your customer support integrations with Knit and focus on delivering a world-class support experience!
📞 Need expert advice? Book a consultation with our team. Find time here
.webp)
Is your EWA platform struggling with complex HRIS and payroll integrations? You're not alone. Learn how a Unified API can automate data flow, ensure accuracy, and help you scale.
Earned Wage Access (EWA) is no longer a novelty; it's a core expectation. Employees want on-demand access to their earned wages, and employers rely on EWA to stand out. But the backbone of any successful EWA platform is its ability to seamlessly, securely, and reliably integrate with diverse HRIS and payroll systems.
This is where Knit, a Unified API platform, comes in. We empower EWA companies to build real-time, secure, and scalable integrations, turning a major operational hurdle into a competitive advantage.
This post explores:
EWA platforms function by giving employees early access to wages they've already earned. To do this effectively, your platform must:
Seamless integrations are the bedrock of accurate deductions, compliance, a superior user experience, and your ability to scale across numerous employer clients without extending the risk of NPAs
Many EWA platforms hit the same walls:
Knit's Approach: We tackle these head-on by providing direct, automated, real-time API integrations wherever they are supported by the payroll providers to ensure a seamless workflow
Let's consider "EarlyWages" (our example EWA platform). They need to integrate with their clients' HRIS/payroll systems to:
.png)
Key Requirement: Deduction APIs must support one-time or dynamic frequencies and allow easy unenrollment to prevent rollovers.
Knit offers standardized, API-driven flows to streamline your EWA operations:
EWA platforms like yours are transforming how employees access their pay. However, unique integration hurdles, especially around timely and accurate deductions, can stifle growth and create operational headaches.
With Knit's Unified API, you unlock a flexible, performant, and secure HRIS and payroll integration foundation. It’s built for the real-time demands of modern EWA, ensuring scalability and peace of mind.
Let Knit handle the integration complexities, so you can focus on what you do best: delivering exceptional Earned Wage Access services.
To get started with Knit's unified Payroll API -You can sign up here or book a demo to talk to an expert
Developer resources on APIs and integrations

Most AI agents hit a wall when they need to take real action. They excel at analysis and reasoning but can't actually update your CRM, create support tickets, or sync employee data. They're essentially trapped in their own sandbox.
The game changes when you combine n8n's new MCP (Model Context Protocol) support with Knit MCP Servers. This combination gives your AI agents secure, production-ready connections to your business applications – from Salesforce and HubSpot to Zendesk and QuickBooks.
This tutorial covers everything you need to build functional AI agents that integrate with your existing business stack:
By following this guide, you'll build an agent that can search your CRM, update contact records, and automatically post summaries to Slack.
The Model Context Protocol (MCP) creates a standardized way for AI models to interact with external tools and data sources. It's like having a universal adapter that connects any AI model to any business application.
n8n's implementation includes two essential components through the n8n-nodes-mcp package:
MCP Client Tool Node: Connects your AI Agent to external MCP servers, enabling actions like "search contacts in Salesforce" or "create ticket in Zendesk"
MCP Server Trigger Node: Exposes your n8n workflows as MCP endpoints that other systems can call
This architecture means your AI agents can perform real business actions instead of just generating responses.
Building your own MCP server sounds appealing until you face the reality:
Knit MCP Servers eliminate this complexity:
✅ Ready-to-use integrations for 100+ business applications
✅ Bidirectional operations – read data and write updates
✅ Enterprise security with compliance certifications
✅ Instant deployment using server URLs and API keys
✅ Automatic updates when SaaS providers change their APIs
Log into your Knit account and navigate to the MCP Hub. This centralizes all your MCP server configurations.
Click "Create New MCP Server" and select your apps :
Choose the exact capabilities your agent needs:
Click "Deploy" to activate your server. Copy the generated Server URL - – you'll need this for the n8n integration.
Create a new n8n workflow and add these essential nodes:
In your MCP Client Tool node:
Your system prompt determines how the agent behaves. Here's a production example:
You are a lead qualification assistant for our sales team.
When given a company domain:
1. Search our CRM for existing contacts at that company
2. If no contacts exist, create a new contact with available information
3. Create a follow-up task assigned to the appropriate sales rep
4. Post a summary to our #sales-leads Slack channel
Always search before creating to avoid duplicates. Include confidence scores in your Slack summaries.
Run the workflow with sample data to verify:
Trigger: New form submission or website visitActions:
Trigger: New support ticket createdActions:
Trigger: New employee added to HRISActions:
Trigger: Invoice status updates
Actions:
Start with 3-5 essential tools rather than overwhelming your agent with every possible action. You can always expand capabilities later.
Structure your prompts to accomplish tasks in fewer API calls:
Add fallback logic for common failure scenarios:
Store all API keys and tokens in n8n's secure credential system, never in workflow prompts or comments.
Limit MCP server tools to only what each agent actually needs:
Enable comprehensive logging to track:
Problem: Agent errors out even when MCP server tool call is succesful
Solutions:
Error: 401/403 responses from MCP server
Solutions:
Use n8n's MCP Server Trigger node to expose your own workflows as MCP tools. This works well for:
However, for standard SaaS integrations, Knit MCP Servers provide better reliability and maintenance.
Connect multiple MCP servers to single agents by adding multiple MCP Client Tool nodes. This enables complex workflows spanning different business systems.
Any language model supported by n8n works with MCP servers, including:
Yes. Add multiple MCP Client Tool nodes to your AI Agent, each connecting to different MCP servers. This enables cross-platform workflows.
No coding required. n8n provides the visual workflow interface, while Knit handles all the API integrations and maintenance.
n8n offers free tiers for basic usage, with paid plans starting around $50/month for teams. Knit MCP pricing varies based on usage and integrations needed
The combination of n8n and Knit MCP Servers transforms AI from a conversation tool into a business automation platform. Your agents can now:
Instead of spending months building custom API integrations, you can:
Ready to build agents that actually work? Start with Knit MCP Servers and see what's possible when AI meets your business applications.

Think of the last time you wished your AI assistant could actually do something instead of just talking about it. Maybe you wanted it to create a GitHub issue, update a spreadsheet, or pull real-time data from your CRM. This is exactly the problem that Model Context Protocol (MCP) servers solve—they transform AI from conversational tools into actionable agents that can interact with your real-world systems.
An MCP server acts as a universal translator between AI models and external tools, enabling AI assistants like Claude, GPT, or Gemini to perform concrete actions rather than just generating text. When properly implemented, MCP servers have helped companies achieve remarkable results: Block reported 25% faster project completion rates, while healthcare providers saw 40% increases in patient engagement through AI-powered workflows.
Since Anthropic introduced MCP in November 2024, the technology has rapidly gained traction with over 200 community-built servers and adoption by major companies including Microsoft, Google, and Block. This growth reflects a fundamental shift from AI assistants that simply respond to questions toward AI agents that can take meaningful actions in business environments.
To appreciate why MCP servers matter, we need to understand the integration challenge that has historically limited AI adoption in business applications. Before MCP, connecting an AI model to external systems required building custom integrations for each combination of AI platform and business tool.
Imagine your organization uses five different AI models and ten business applications. Traditional approaches would require building fifty separate integrations—what developers call the "N×M problem." Each integration needs custom authentication logic, error handling, data transformation, and maintenance as APIs evolve.
This complexity created a significant barrier to AI adoption. Development teams would spend months building and maintaining custom connectors, only to repeat the process when adding new tools or switching AI providers. The result was that most organizations could only implement AI in isolated use cases rather than comprehensive, integrated workflows.
MCP servers eliminate this complexity by providing a standardized protocol that reduces integration requirements from N×M to N+M. Instead of building fifty custom integrations, you deploy ten MCP servers (one per business tool) that any AI model can use. This architectural improvement enables organizations to deploy new AI capabilities in days rather than months while maintaining consistency across different AI platforms.
Understanding MCP's architecture helps explain why it succeeds where previous integration approaches struggled. At its foundation, MCP uses JSON-RPC 2.0, a proven communication protocol that provides reliable, structured interactions between AI models and external systems.
The protocol operates through three fundamental primitives that AI models can understand and utilize naturally. Tools represent actions the AI can perform—creating database records, sending notifications, or executing automated workflows. Resources provide read-only access to information—documentation, file systems, or live metrics that inform AI decision-making. Prompts offer standardized templates for common interactions, ensuring consistent AI behavior across teams and use cases.
The breakthrough innovation lies in dynamic capability discovery. When an AI model connects to an MCP server, it automatically learns what functions are available without requiring pre-programmed knowledge. This means new integrations become immediately accessible to AI agents, and updates to backend systems don't break existing workflows.
Consider how this works in practice. When you deploy an MCP server for your project management system, any connected AI agent can automatically discover available functions like "create task," "assign team member," or "generate status report." The AI doesn't need specific training data about your project management tool—it learns the capabilities dynamically and can execute complex, multi-step workflows based on natural language instructions.
Transport mechanisms support different deployment scenarios while maintaining protocol consistency. STDIO transport enables secure, low-latency local connections perfect for development environments. HTTP with Server-Sent Events supports remote deployments with real-time streaming capabilities. The newest streamable HTTP transport provides enterprise-grade performance for production systems handling high-volume operations.
The most successful MCP implementations solve practical business challenges rather than showcasing technical capabilities. Developer workflow integration represents the largest category of deployments, with platforms like VS Code, Cursor, and GitHub Copilot using MCP servers to give AI assistants comprehensive understanding of development environments.
Block's engineering transformation exemplifies this impact. Their MCP implementation connects AI agents to internal databases, development platforms, and project management systems. The integration enables AI to handle routine tasks like code reviews, database queries, and deployment coordination automatically. The measurable result—25% faster project completion rates—demonstrates how MCP can directly improve business outcomes.
Design-to-development workflows showcase MCP's ability to bridge creative and technical processes. When Figma released their MCP server, it enabled AI assistants in development environments to extract design specifications, color palettes, and component hierarchies directly from design files. Designers can now describe modifications in natural language and watch AI generate corresponding code changes automatically, eliminating the traditional handoff friction between design and development teams.
Enterprise data integration represents another transformative application area. Apollo GraphQL's MCP server exemplifies this approach by making complex API schemas accessible through natural language queries. Instead of requiring developers to write custom GraphQL queries, business users can ask questions like "show me all customers who haven't placed orders in the last quarter" and receive accurate data without technical knowledge.
Healthcare organizations have achieved particularly impressive results by connecting patient management systems through MCP servers. AI chatbots can now access real-time medical records, appointment schedules, and billing information to provide comprehensive patient support. The 40% increase in patient engagement reflects how MCP enables more meaningful, actionable interactions rather than simple question-and-answer exchanges.
Manufacturing and supply chain applications demonstrate MCP's impact beyond software workflows. Companies use MCP-connected AI agents to monitor inventory levels, predict demand patterns, and coordinate supplier relationships automatically. The 25% reduction in inventory costs achieved by early adopters illustrates how AI can optimize complex business processes when properly integrated with operational systems.
The primary advantage of MCP servers extends beyond technical convenience to fundamental business value creation. Integration standardization eliminates the custom development overhead that has historically limited AI adoption in enterprise environments. Development teams can focus on business logic rather than building and maintaining integration infrastructure.
This standardization creates a multiplier effect for AI initiatives. Each new MCP server deployment increases the capabilities of all connected AI agents simultaneously. When your organization adds an MCP server for customer support tools, every AI assistant across different departments can leverage those capabilities immediately without additional development work.
Semantic abstraction represents another crucial business benefit. Traditional APIs expose technical implementation details—cryptic field names, status codes, and data structures designed for programmers rather than business users. MCP servers translate these technical interfaces into human-readable parameters that AI models can understand and manipulate intuitively.
For example, creating a new customer contact through a traditional API might require managing dozens of technical fields with names like "custom_field_47" or "status_enum_id." An MCP server abstracts this complexity, enabling AI to create contacts using natural parameters like createContact(name: "Sarah Johnson", company: "Acme Corp", status: "active"). This abstraction makes AI interactions more reliable and reduces the expertise required to implement complex workflows.
The stateful session model enables sophisticated automation that would be difficult or impossible with traditional request-response APIs. AI agents can maintain context across multiple tool invocations, building up complex workflows step by step. An agent might analyze sales performance data, identify concerning trends, generate detailed reports, create presentation materials, and schedule team meetings to discuss findings—all as part of a single, coherent workflow initiated by a simple natural language request.
Security and scalability benefits emerge from implementing authentication and access controls at the protocol level rather than in each custom integration. MCP's OAuth 2.1 implementation with mandatory PKCE provides enterprise-grade security that scales automatically as you add new integrations. The event-driven architecture supports real-time updates without the polling overhead that can degrade performance in traditional integration approaches.
Successful MCP server deployment requires choosing the right architectural pattern for your organization's needs and constraints. Local development patterns serve individual developers who want to enhance their development environment capabilities. These implementations run MCP servers locally using STDIO transport, providing secure access to file systems and development tools without network dependencies or security concerns.
Remote production patterns suit enterprise deployments where multiple team members need consistent access to AI-enhanced workflows. These implementations deploy MCP servers as containerized microservices using HTTP-based transports with proper authentication and can scale automatically based on demand. Remote patterns enable organization-wide AI capabilities while maintaining centralized security and compliance controls.
Hybrid integration patterns combine local and remote servers for complex scenarios that require both individual productivity enhancement and enterprise system integration. Development teams might use local MCP servers for file system access and code analysis while connecting to remote servers for shared business systems like customer databases or project management platforms.
The ecosystem provides multiple implementation pathways depending on your technical requirements and available resources. The official Python and TypeScript SDKs offer comprehensive protocol support for organizations building custom servers tailored to specific business requirements. These SDKs handle the complex protocol details while providing flexibility for unique integration scenarios.
High-level frameworks like FastMCP significantly reduce development overhead for common server patterns. With FastMCP, you can implement functional MCP servers in just a few lines of code, making it accessible to teams without deep protocol expertise. This approach works well for straightforward integrations that follow standard patterns.
For many organizations, pre-built community servers eliminate custom development entirely. The MCP ecosystem includes professionally maintained servers for popular business applications like GitHub, Slack, Google Workspace, and Salesforce. These community servers undergo continuous testing and improvement, often providing more robust functionality than custom implementations.
Enterprise managed platforms like Knit represent the most efficient deployment path for organizations prioritizing rapid time-to-value over custom functionality. Rather than managing individual MCP servers for each business application, platforms like Knit's unified MCP server combine related APIs into comprehensive packages. For example, a single Knit deployment might integrate your entire HR technology stack—recruitment platforms, payroll systems, performance management tools, and employee directories—into one coherent MCP server that AI agents can use seamlessly.
Major technology platforms are building native MCP support to reduce deployment friction. Claude Desktop provides built-in MCP client capabilities that work with any compliant server. VS Code and Cursor offer seamless integration through extensions that automatically discover and configure available MCP servers. Microsoft's Windows 11 includes an MCP registry system that enables system-wide AI tool discovery and management.
MCP server deployments introduce unique security challenges that require careful consideration and proactive management. The protocol's role as an intermediary between AI models and business-critical systems creates potential attack vectors that don't exist in traditional application integrations.
Authentication and authorization form the security foundation for any MCP deployment. The latest MCP specification adopts OAuth 2.1 with mandatory PKCE (Proof Key for Code Exchange) for all client connections. This approach prevents authorization code interception attacks while supporting both human user authentication and machine-to-machine communication flows that automated AI agents require.
Implementing the principle of least privilege becomes especially critical when AI agents gain broad access to organizational systems. MCP servers should request only the minimum permissions necessary for their intended functionality and implement additional access controls based on user context, time restrictions, and business rules. Many security incidents in AI deployments result from overprivileged service accounts that exceed their intended scope and provide excessive access to automated systems.
Data handling and privacy protection require special attention since MCP servers often aggregate access to multiple sensitive systems simultaneously. The most secure architectural pattern involves event-driven systems that process data in real-time without persistent storage. This approach eliminates data breach risks associated with stored credentials or cached business information while maintaining the real-time capabilities that make AI agents effective in business environments.
Enterprise deployments should implement comprehensive monitoring and audit trails for all MCP server activities. Every tool invocation, resource access attempt, and authentication event should be logged with sufficient detail to support compliance requirements and security investigations. Structured logging formats enable automated security monitoring systems to detect unusual patterns or potential misuse of AI agent capabilities.
Network security considerations include enforcing HTTPS for all communications, implementing proper certificate validation, and using network policies to restrict server-to-server communications. Container-based MCP server deployments should follow security best practices including running as non-root users, using minimal base images, and implementing regular vulnerability scanning workflows.
The MCP ecosystem offers multiple deployment approaches, each optimized for different organizational needs, technical constraints, and business objectives. Understanding these options helps organizations make informed decisions that align with their specific requirements and capabilities.
Open source solutions like the official reference implementations provide maximum customization potential and benefit from active community development. These solutions work well for organizations with strong technical teams who need specific functionality or have unique integration requirements. However, open source deployments require ongoing maintenance, security management, and protocol updates that can consume significant engineering resources over time.
Self-hosted commercial platforms offer professional support and enterprise features while maintaining organizational control over data and deployment infrastructure. These solutions suit large enterprises with specific compliance requirements, existing infrastructure investments, or regulatory constraints that prevent cloud-based deployments. Self-hosted platforms typically provide better customization options than managed services but require more operational expertise and infrastructure management.
Managed MCP services eliminate operational overhead by handling server hosting, authentication management, security updates, and protocol compliance automatically. This approach enables organizations to focus on business value creation rather than infrastructure management. Managed platforms typically offer faster time-to-value and lower total cost of ownership, especially for organizations without dedicated DevOps expertise.
The choice between these approaches often comes down to integration breadth versus operational complexity. Building and maintaining individual MCP servers for each external system essentially recreates the integration maintenance burden that MCP was designed to eliminate. Organizations that need to integrate with dozens of business applications may find themselves managing more infrastructure complexity than they initially anticipated.
Unified integration platforms like Knit address this challenge by packaging related APIs into comprehensive, professionally maintained servers. Instead of deploying separate MCP servers for your project management tool, communication platform, file storage system, and authentication provider, a unified platform combines these into a single, coherent server that AI agents can use seamlessly. This approach significantly reduces the operational complexity while providing broader functionality than individual server deployments.
Authentication complexity represents another critical consideration in solution selection. Managing OAuth flows, token refresh cycles, and permission scopes across dozens of different services requires significant security expertise and creates ongoing maintenance overhead. Managed platforms abstract this complexity behind standardized authentication interfaces while maintaining enterprise-grade security controls and compliance capabilities.
For organizations prioritizing rapid deployment and minimal maintenance overhead, managed solutions like Knit's comprehensive MCP platform provide the fastest path to AI-powered workflows. Organizations with specific security requirements, existing infrastructure investments, or unique customization needs may prefer self-hosted options despite the additional operational complexity they introduce.
Successfully implementing MCP servers requires a structured approach that balances technical requirements with business objectives. The most effective implementations start with specific, measurable use cases rather than attempting comprehensive deployment across all organizational systems simultaneously.
Phase one should focus on identifying a high-impact, low-complexity integration that can demonstrate clear business value. Common starting points include enhancing developer productivity through IDE integrations, automating routine customer support tasks, or streamlining project management workflows. These use cases provide tangible benefits while allowing teams to develop expertise with MCP concepts and deployment patterns.
Technology selection during this initial phase should prioritize proven solutions over cutting-edge options. For developer-focused implementations, pre-built servers for GitHub, VS Code, or development environment tools offer immediate value with minimal setup complexity. Organizations focusing on business process automation might start with servers for their project management platform, communication tools, or document management systems.
The authentication and security setup process requires careful planning to ensure scalability as deployments expand. Organizations should establish OAuth application registrations, define permission scopes, and implement audit logging from the beginning rather than retrofitting security controls later. This foundation becomes especially important as MCP deployments expand to include more sensitive business systems.
Integration testing should validate both technical functionality and end-to-end business workflows. Protocol-level testing tools like MCP Inspector help identify communication issues, authentication problems, or malformed requests before production deployment. However, the most important validation involves testing actual business scenarios—can AI agents complete the workflows that provide business value, and do the results meet quality and accuracy requirements?
Phase two expansion can include broader integrations and more complex workflows based on lessons learned during initial deployment. Organizations typically find that success in one area creates demand for similar automation in adjacent business processes. This organic growth pattern helps ensure that MCP deployments align with actual business needs rather than pursuing technology implementation for its own sake.
For organizations seeking to minimize implementation complexity while maximizing integration breadth, platforms like Knit provide comprehensive getting-started resources that combine multiple business applications into unified MCP servers. This approach enables organizations to deploy extensive AI capabilities in hours rather than weeks while benefiting from professional maintenance and security management.
Even well-planned MCP implementations encounter predictable challenges that organizations can address proactively with proper preparation and realistic expectations. Integration complexity represents the most common obstacle, especially when organizations attempt to connect AI agents to legacy systems with limited API capabilities or inconsistent data formats.
Performance and reliability concerns emerge when MCP servers become critical components of business workflows. Unlike traditional applications where users can retry failed operations manually, AI agents require consistent, reliable access to external systems to complete automated workflows successfully. Organizations should implement proper error handling, retry logic, and fallback mechanisms to ensure robust operation.
User adoption challenges often arise when AI-powered workflows change established business processes. Successful implementations invest in user education, provide clear documentation of AI capabilities and limitations, and create gradual transition paths rather than attempting immediate, comprehensive workflow changes.
Scaling complexity becomes apparent as organizations expand from initial proof-of-concept deployments to enterprise-wide implementations. Managing authentication credentials, monitoring system performance, and maintaining consistent AI behavior across multiple integrated systems requires operational expertise that many organizations underestimate during initial planning.
Managed platforms like Knit address many of these challenges by providing professional implementation support, ongoing maintenance, and proven scaling patterns. Organizations can benefit from the operational expertise and lessons learned from multiple enterprise deployments rather than solving common problems independently.
MCP servers represent a fundamental shift in how organizations can leverage AI technology to improve business operations. Rather than treating AI as an isolated tool for specific tasks, MCP enables AI agents to become integral components of business workflows with the ability to access live data, execute actions, and maintain context across complex, multi-step processes.
The technology's rapid adoption reflects its ability to solve real business problems rather than showcase technical capabilities. Organizations across industries are discovering that standardized AI-tool integration eliminates the traditional barriers that have limited AI deployment in mission-critical business applications.
Early indicators suggest that organizations implementing comprehensive MCP strategies will develop significant competitive advantages as AI becomes more sophisticated and capable. The businesses that establish AI-powered workflows now will be positioned to benefit immediately as AI models become more powerful and reliable.
For development teams and engineering leaders evaluating AI integration strategies, MCP servers provide the standardized foundation needed to move beyond proof-of-concept demonstrations toward production systems that transform how work gets accomplished. Whether you choose to build custom implementations, deploy community servers, or leverage managed platforms like Knit's comprehensive MCP solutions, the key is establishing this foundation before AI capabilities advance to the point where integration becomes a competitive necessity rather than a strategic advantage.
The organizations that embrace MCP-powered AI integration today will shape the future of work in their industries, while those that delay adoption may find themselves struggling to catch up as AI-powered automation becomes the standard expectation for business efficiency and effectiveness.
.webp)
Welcome to our comprehensive guide on troubleshooting common Salesforce integration challenges. Whether you're facing authentication issues, configuration errors, or data synchronization problems, this FAQ provides step-by-step instructions to help you debug and fix these issues.
Building a Salesforce Integration? Learn all about the Salesforce API in our in-depth Salesforce Integration Guide
Resolution: Refresh your token if needed, update your API endpoint to the proper instance, and adjust session or Connected App settings as required.
Resolution: Correct any mismatches in credentials or settings and restart the OAuth process to obtain fresh tokens.
Resolution: Integrate an automatic token refresh process to ensure seamless generation of a new access token when needed.
Resolution: Reconfigure your Connected App as needed and test until you receive valid tokens.
Resolution: Adjust your production settings to mirror your sandbox configuration and update any environment-specific parameters.
Resolution: Follow Salesforce’s guidelines, test in a sandbox, and ensure all endpoints and metadata are exchanged correctly.
Resolution: Correct the field names and update permissions so the integration user can access the required data.
Resolution: Adjust your integration to enforce proper ID formatting and validate IDs before using them in API calls.
Resolution: Update user permissions and sharing settings to ensure all referenced data is accessible.
Resolution: Choose REST for lightweight web/mobile applications and SOAP for enterprise-level integrations that require robust transaction support.
Resolution: Integrate the Bulk API using available libraries or custom HTTP requests, ensuring continuous monitoring of job statuses.
Resolution: Ensure the JWT is correctly formatted and securely signed, then follow Salesforce documentation to obtain your access token.
Resolution: Develop your mobile integration with Salesforce’s mobile tools, ensuring robust authentication and data synchronization.
Resolution: Refactor your integration to minimize API calls and use smart retry logic to handle rate limits gracefully.
Resolution: Develop a layered logging system that captures detailed data while protecting sensitive information.
Resolution: Establish a robust logging framework for real-time monitoring and proactive error resolution.
Resolution: Adopt middleware that matches your requirements for secure, accurate, and efficient data exchange.
Resolution: Enhance your data sync strategy with incremental updates and conflict resolution to ensure data consistency.
Resolution: Use secure storage combined with robust access controls to protect your OAuth tokens.
Resolution: Strengthen your security by combining narrow OAuth scopes, IP restrictions, and dedicated integration user accounts.
Resolution: Follow Salesforce best practices to secure credentials, manage tokens properly, and design your integration for scalability and reliability.
If you're finding it challenging to build and maintain these integrations on your own, Knit offers a seamless, managed solution. With Knit, you don’t have to worry about complex configurations, token management, or API limits. Our platform simplifies Salesforce integrations, so you can focus on growing your business.
Stop spending hours troubleshooting and maintaining complex integrations. Discover how Knit can help you seamlessly connect Salesforce with your favorite systems—without the hassle. Explore Knit Today »
Deep dives into the Knit product and APIs

Are you in the market for Nango alternatives that can power your API integration solutions? In this article, we’ll explore five top platforms—Knit, Merge.dev, Apideck, Paragon, and Tray Embedded—and dive into their standout features, pros, and cons. Discover why Knit has become the go-to option for B2B SaaS integrations, helping companies simplify and secure their customer-facing data flows.
Nango is an open-source embedded integration platform that helps B2B SaaS companies quickly connect various applications via a single interface. Its streamlined setup and developer-friendly approach can accelerate time-to-market for customer-facing integrations. However, coverage is somewhat limited compared to broader unified API platforms—particularly those offering deeper category focus and event-driven architectures.
Nango also relies heavily on open source communities for adding new connectors which makes connector scaling less predictable fo complex or niche use cases.
Pros (Why Choose Nango):
Cons (Challenges & Limitations):
Now let’s look at a few Nango alternatives you can consider for scaling your B2B SaaS integrations, each with its own unique blend of coverage, security, and customization capabilities.

Overview
Knit is a unified API platform specifically tailored for B2B SaaS integrations. By consolidating multiple applications—ranging from CRM to HRIS, Recruitment, Communication, and Accounting—via a single API, Knit helps businesses reduce the complexity of API integration solutions while improving efficiency.
Key Features
Pros

Overview
Merge.dev delivers unified APIs for crucial categories like HR, payroll, accounting, CRM, and ticketing systems—making it a direct contender among top Nango alternatives.
Key Features
Pros
Cons

Overview
Apideck offers a suite of API integration solutions that give developers access to multiple services through a single integration layer. It’s well-suited for categories like HRIS and ATS.
Key Features
Pros
Cons

Overview
Paragon is an embedded integration platform geared toward building and managing customer-facing integrations for SaaS businesses. It stands out with its visual workflow builder, enabling lower-code solutions.
Key Features
Pros
Cons

Overview
Tray Embedded is another formidable competitor in the B2B SaaS integrations space. It leverages a visual workflow builder to enable embedded, native integrations that clients can use directly within their SaaS platforms.
Key Features
Pros
Cons
When searching for Nango alternatives that offer a streamlined, secure, and B2B SaaS-focused integration experience, Knit stands out. Its unified API approach and event-driven architecture protect end-user data while accelerating the development process. For businesses seeking API integration solutions that minimize complexity, boost security, and enhance scalability, Knit is a compelling choice.
.webp)
Whether you’re a SaaS founder, product manager, or part of the customer success team, one thing is non-negotiable — customer data privacy. If your users don’t trust how you handle data, especially when integrating with third-party tools, it can derail deals and erode trust.
Unified APIs have changed the game by letting you launch integrations faster. But under the hood, not all unified APIs work the same way — and Kombo.dev and Knit.dev take very different approaches, especially when it comes to data sync, compliance, and scalability.
Let’s break it down.
Unified APIs let you integrate once and connect with many applications (like HR tools, CRMs, or payroll systems). They normalize different APIs into one schema so you don’t have to build from scratch for every tool.
A typical unified API has 4 core components:
This makes Knit ideal if you care about branding and custom UX.
Tom summarize, Knit API is the only unified API that does not store customer data at our end, and offers a scalable, secure, event-driven push data sync architecture for smaller as well as larger data loads.By now, if you are convinced that Knit API is worth giving a try, please click here to get your API keys. Or if you want to learn more, see our docs
Our detailed guides on the integrations space
.png)
Now that we understand the fundamentals of the Model Context Protocol (MCP) i.e. what it is and how it works, it’s time to delve deeper.
One of the simplest, most effective ways to begin your MCP journey is by implementing a “one agent, one server” integration. This approach forms the foundation of many real-world MCP deployments and is ideal for both newcomers and experienced developers looking to quickly prototype tool-augmented agents.
In this guide, we’ll walk through:
In the “one agent, one server” architecture, a single AI agent (the MCP client) communicates with one MCP-compliant server that exposes tools for a particular task or domain. All requests for external knowledge, actions, or computations pass through this centralized server.
This model acts like a dedicated plugin or assistant API layer that the AI can call upon when it needs structured help. It is:
Think of it as building a custom toolbox for your agent, tailored to solve a specific category of problems, whether that’s answering product support queries, reading documents from a Git repo, or retrieving contact info from your CRM.
Here’s how it works:
This pattern is straightforward, scalable, and offers a gentle learning curve into the MCP ecosystem.
Imagine a chatbot deployed to support internal staff or customers. This bot connects to an MCP server offering:
When a user asks a support question, the agent can query the MCP server and surface the answer from verified documentation in real-time, enabling precise and context-rich responses.
A coding assistant might rely on an MCP server integrated with GitHub. The tools it exposes may include:
With these tools, the AI assistant can fetch file contents, analyze open issues, or suggest improvements across repositories—without hardcoding API logic.
Sales AI agents benefit from structured access to CRM systems like Salesforce. A single MCP server might provide tools such as:
This enables natural-language queries like “What’s the latest interaction with contact@example.com?” to be resolved with precise data pulled from the CRM backend, all via the MCP protocol.
A virtual sales assistant can streamline backend retail operations using an MCP server connected to inventory and ordering systems. The server might provide tools such as:
With this setup, the assistant can respond to queries like “Is product X in stock?” or “Order 200 units of item Y for customer Z,” ensuring fast, error-free operations without requiring manual database access.
5. Internal DevOps Monitoring for IT Assistants
An internal DevOps assistant can manage infrastructure health through an MCP interface linked to monitoring systems. Key tools might include:
This empowers IT teams to ask, “Is the database server down?” or instruct, “Restart the authentication service,” all via natural language, reducing downtime and improving operational responsiveness with minimal manual intervention.
Example: A customer support agent loads a local MCP server that wraps the documentation backend.
Example: The manifest reveals search_docs(query) and fetch_article(article_id) tools.
Example: A user asks a technical question, and the agent opts to invoke search_docs.
Example: { "tool_name": "search_docs", "args": { "query": "reset password instructions" } }
Example: It fetches the correct answer from documentation and returns it in natural language.
Everything flows through a single, standardized protocol, dramatically reducing the complexity of integration and tool management.
This single-server pattern is ideal when:
Single-server integrations are significantly faster to prototype and deploy. You only need to manage one connection, one manifest, and one set of tool definitions. This simplicity is especially valuable for teams new to MCP or for iterating quickly.
When a server exposes only one capability domain (e.g., CRM data, GitHub interactions), it creates natural boundaries. This improves maintainability, clarity of purpose, and reduces coupling between systems.
Since the AI agent never has to know how the tool is implemented, you can wrap any existing backend API or internal logic behind the MCP interface. This can be achieved without rewriting application logic or embedding credentials into your agent.
Even with one tool, you benefit from MCP’s typed, introspectable communication format. This makes it easier to later swap out implementations, integrate observability, or reuse the tool interface in other agents or systems.
You can test your MCP server independently of the AI agent. Logging the requests and responses from a single tool invocation makes it easier to identify and resolve bugs in isolation.
With a single MCP server, there’s no need for complex orchestration layers, service registries, or load balancers. You can run your integration on a lightweight stack. This is ideal for early-stage development, internal tools, or proof-of-concept deployments.
By reducing configuration, coordination, and deployment steps, single-server MCP setups let teams roll out AI capabilities quickly. Whether you’re launching an internal agent or a customer-facing assistant, you can go from idea to functional prototype in just a few days.
It’s tempting to pack multiple unrelated tools into one server. This reduces modularity and defeats the purpose of scoping. For long-term scalability, each server should handle a cohesive set of responsibilities.
Even in early projects, it’s crucial to think about tool versioning. Changes in input/output schemas can break agent behavior. Establish a convention for tool versions and communicate them through the manifest.
MCP expects structured tool responses. If your tool implementation returns malformed or inconsistent outputs, the agent may fail unpredictably. Use schema validation libraries to enforce correctness.
Many developers hardcode the server transport type (e.g., HTTP, stdio) or endpoints. This limits portability. Ideally, the client should accept configurable endpoints, enabling easy switching between local dev, staging, and production environments.
It’s important to log each tool call, input, and response, especially for production use. Without this, debugging agent behavior becomes much harder when things go wrong.
Without proper error handling, failed tool calls may go unnoticed, causing the agent to hang or behave unpredictably. Always define timeouts, catch exceptions, and return structured error messages to keep the agent responsive and resilient under failure conditions.
Just because a tool seems intuitive to a developer doesn’t mean the agent will use it correctly. Clear metadata, like names, descriptions, input types, and examples, to help the agent choose and use tools effectively, improving reliability and user outcomes.
MCP supports different transport mechanisms, including stdio, HTTP, and WebSocket. Starting with run_stdio() makes it easier to test locally without the complexity of networking or authentication.
The better you describe the tool (name, description, parameters), the more accurately the AI agent can use it. Think of the tool metadata as an API contract between human developers and AI agents.
Maintain proper documentation of each tool’s purpose, expected parameters, and return values. This helps in agent tuning and improves collaboration among development teams.
Even though the MCP protocol abstracts away the implementation, you can help guide your agent’s behavior by priming it with examples of how tools are used, what outputs look like, and when to invoke them.
Design unit tests for each tool implementation. You can simulate MCP calls and verify correct results and schema adherence. This becomes especially valuable in CI/CD pipelines when evolving your server.
Even in single-server setups, it pays to structure your codebase for future growth. Use modular patterns, define clear tool interfaces, and separate logic by domain. This makes it easier to split functionality into multiple servers as your system evolves.
Tool names should clearly describe what they do using verbs and nouns (e.g., get_invoice_details). Avoid internal jargon or overly verbose labels, concise, action-based names improve agent comprehension and reduce invocation errors.
Capturing input/output logs for each tool invocation is essential for debugging and observability. Use structured formats like JSON to make logs easily searchable and integrable with monitoring pipelines or alert systems.
Starting with a single MCP server is the fastest, cleanest way to build powerful AI agents that interact with real-world systems. It’s simple enough for small experiments, but standardized enough to grow into complex, multi-server deployments when you’re ready.
By adhering to best practices and avoiding common pitfalls, you set yourself up for long-term success in building tool-augmented AI agents.
Whether you’re enhancing an existing assistant, launching a new AI product, or just exploring the MCP ecosystem, the single-server pattern is a foundational building block and an ideal starting point for anyone serious about intelligent, extensible agents.
1. Why should I start with a single-server MCP integration instead of multiple servers or tools?
Single-server setups are easier to prototype, debug, and deploy. They reduce complexity, require minimal infrastructure, and help you focus on mastering the MCP workflow before scaling.
2. What types of use cases are best suited for single-server MCP architectures?
They’re ideal for domain-specific tasks like customer support document retrieval, CRM lookups, DevOps monitoring, or repository interaction, where one set of tools can fulfill most requests.
3. How do I structure the tools exposed by the MCP server?
Keep tools focused on a single domain. Use clear, action-oriented names (e.g., search_docs, get_account_details) and provide strong metadata so agents can invoke them accurately.
4. Can I expose multiple tools from the same server?
Yes, but only if they serve a cohesive purpose within the same domain. Avoid mixing unrelated tools, which can reduce maintainability and confuse the agent’s decision-making process.
5. What’s the best way to test my MCP server locally before connecting it to an agent?
Use run_stdio() to start a local MCP server. It’s ideal for development since it avoids network setup and lets you quickly validate tool invocation logic.
6. How does the AI agent know which tool to call from the server?
The agent receives a tool manifest from the MCP server that includes names, input/output schemas, and descriptions. It uses this metadata to decide which tool to invoke based on user input.
7. What should I log when running a single-server MCP setup?
Log every tool invocation with input parameters, output responses, and errors, preferably in structured JSON. This simplifies debugging and improves observability.
8. What are common mistakes to avoid in a single-server integration?
Avoid overloading the server with unrelated tools, skipping schema validation, hardcoding endpoints, ignoring tool versioning, and failing to implement error handling or timeouts.
9. How do I handle changes to tools without breaking the agent?
Use versioning in your tool names or metadata (e.g., get_contact_v2). Clearly document input/output schema changes and update your manifest accordingly to maintain backward compatibility.
10. Can I scale from a single-server setup to a multi-server architecture later?
Absolutely. Designing your tools with modularity and clean interfaces from the start allows for easy migration to multi-server architectures as your use case grows.
.png)
The Model Context Protocol (MCP) is still in its early days, but it has an active community and a roadmap pointing towards significant enhancements. Since Anthropic introduced this open standard in November 2024, MCP has rapidly evolved from an experimental protocol to a cornerstone technology that promises to reshape the AI landscape. As we examine the roadmap ahead, it's clear that MCP is not just another API standard. Rather, it's the foundation for a new era of interconnected, context-aware AI systems.
Before exploring what lies ahead, it's essential to understand where MCP stands today. The protocol has experienced explosive growth, with thousands of MCP servers developed by the community and increasing enterprise adoption. The ecosystem has expanded to include integrations with popular tools like GitHub, Slack, Google Drive, and enterprise systems, demonstrating MCP's versatility across diverse use cases.
Understanding the future direction of MCP can help teams plan their adoption strategy and anticipate new capabilities. Many planned features directly address current limitations. Here's a look at key areas of development for MCP based on public roadmaps and community discussions.
Read more: The Pros and Cons of Adopting MCP Today
The MCP roadmap focuses on unlocking scale, security, and extensibility across the ecosystem.
The most significant enhancement on MCP's roadmap is comprehensive support for remote servers. Currently, MCP primarily operates through local stdio connections, which limits its scalability and enterprise applicability. The roadmap prioritizes several critical developments:
One of the most transformative elements of the MCP roadmap is the development of a centralized MCP Registry. This discovery service will function as the "app store" for MCP servers, enabling:
Microsoft has already demonstrated early registry concepts with their Azure API Center integration for MCP servers, showing how enterprises can maintain private registries while benefiting from the broader ecosystem.
The future of MCP extends far beyond simple client-server interactions. The roadmap includes substantial enhancements for multi-agent systems and complex orchestrations:
Read more: Scaling AI Capabilities: Using Multiple MCP Servers with One Agent
Security remains a paramount concern as MCP scales to enterprise adoption. The roadmap addresses this through multiple initiatives:
The MCP ecosystem's maturity depends on high-quality reference implementations and robust testing frameworks:
The roadmap recognizes that protocol success depends on supporting tools and infrastructure:
As MCP matures, its governance model is becoming more structured to ensure the protocol remains an open standard:
As MCP evolves from a niche protocol to a foundational layer for context-aware AI systems, its implications stretch across engineering, product, and enterprise leadership. Understanding what MCP enables and how to prepare for it can help organizations and teams stay ahead of the curve.
MCP introduces a composable, protocol-driven approach to building AI systems that is significantly more scalable and maintainable than bespoke integrations.
Key Benefits:
How to Prepare:
MCP offers PMs a unified, open foundation for embedding AI capabilities across product experiences—without the risk of vendor lock-in or massive rewrites down the line.
Key Opportunities:
How to Prepare:
For enterprises, MCP represents the potential for secure, scalable, and governable AI deployment across internal and customer-facing applications.
Strategic Advantages:
How to Prepare:
MCP also introduces a new layer of control and coordination for data and AI/ML teams building LLM-powered experiences or autonomous systems.
What it Enables:
How to Prepare:
Ultimately, MCP adoption is a cross-functional effort. Developers, product leaders, security architects, and AI strategists all stand to gain, but also must align.
Best Practices for Collaboration:
The trajectory of MCP adoption suggests significant market transformation ahead. Industry analysts project that the MCP server market could reach $10.3 billion by 2025, with a compound annual growth rate of 34.6%. This growth is driven by several factors:
Despite its promising future, MCP faces several challenges that could impact its trajectory:
The rapid proliferation of MCP servers has raised security concerns. Research by Equixly found command injection vulnerabilities in 43% of tested MCP implementations, with additional concerns around server-side request forgery and arbitrary file access. The roadmap's focus on enhanced security measures directly addresses these concerns, but implementation will be crucial.
While MCP shows great promise, current enterprise adoption faces hurdles. Organizations need more than just protocol standardization, they require comprehensive governance, policy enforcement, and integration with existing enterprise architectures. The roadmap addresses these needs, but execution remains challenging.
As MCP evolves to support more sophisticated use cases, there's a risk of increasing complexity that could hinder adoption. The challenge lies in providing advanced capabilities while maintaining the simplicity that makes MCP attractive to developers.
The emergence of competing protocols like Google's Agent2Agent (A2A) introduces potential fragmentation risks. While A2A positions itself as complementary to MCP, focusing on agent-to-agent communication rather than tool integration, the ecosystem must navigate potential conflicts and overlaps.
The future of MCP is already taking shape through early implementations and pilot projects:
The next five years will be crucial for MCP's evolution from promising protocol to industry standard. Several trends will shape this journey:
MCP is expected to achieve full standardization by 2026, with stable specifications and comprehensive compliance frameworks. This maturity will enable broader enterprise adoption and integration with existing technology stacks.
As AI agents become more sophisticated and autonomous, MCP will serve as the foundational infrastructure enabling their interaction with the digital world. The protocol's support for multi-agent orchestration positions it well for this future.
MCP will likely integrate with emerging technologies like blockchain for trust and verification, edge computing for distributed AI deployment, and quantum computing for enhanced security protocols.
The MCP ecosystem will likely see consolidation as successful patterns emerge and standardized solutions replace custom implementations. This consolidation will reduce complexity while increasing reliability and security.
MCP is on track to redefine how AI systems interact with tools, data, and each other. With industry backing, active development, and a clear technical direction, it’s well-positioned to become the backbone of context-aware, interconnected AI. The next phase will determine whether MCP achieves its bold vision of becoming the universal standard for AI integration, but its momentum suggests a transformative shift in how AI applications are built and deployed.
Wondering whether going the MCP route is right? Check out: Should You Adopt MCP Now or Wait? A Strategic Guide
Q1. Will MCP support policy-based routing of agent requests?
Yes. Future versions of MCP aim to support policy-based routing mechanisms where agent requests can be dynamically directed to different servers or tools based on contextual metadata (e.g., region, user role, workload type). This will enable more intelligent orchestration in regulated or performance-sensitive environments.
Q2. Can MCP be embedded into edge or on-device AI applications?
The roadmap includes lightweight, resource-efficient implementations of MCP that can run on edge devices, enabling offline or low-latency deployments, especially for industrial IoT, wearable tech, and privacy-critical applications.
Q3. How will MCP handle compliance with data protection regulations like GDPR or HIPAA?
MCP governance groups are exploring built-in mechanisms to support data residency, consent tracking, and audit logging to comply with regulatory frameworks. Expect features like context-specific data handling policies and pluggable compliance modules by MCP 2.0.
Q4. Will MCP support version pinning for tools and agents?
Yes. Future registry specifications will allow developers to pin specific versions of tools or agents, ensuring compatibility and stability across environments. This will also enable reproducible workflows and better CI/CD practices for AI.
Q5. Will there be MCP-native billing or monetization models for third-party servers?
Long-term roadmap discussions include API-level support for metering and monetization. MCP Registry may eventually integrate billing capabilities, allowing third-party tool developers to monetize server usage via subscriptions or usage-based models.
Q6. Can MCP integrate with real-time collaboration tools like Figma or Miro?
Multimodal and real-time streaming support opens up integration possibilities with collaborative design, whiteboarding, and visualization tools. Several proof-of-concept implementations are underway to test these interactions in multi-agent design and research workflows.
Q7. Will MCP support context portability across different agents or sessions?
Yes. The concept of “context containers” or “context snapshots” is under development. These would allow persistent, portable contexts that can be passed across agents, sessions, or devices while maintaining traceability and state continuity.
Q8. How will MCP evolve to support AI safety and alignment research?
Dedicated working groups are exploring how MCP can natively support mechanisms like human override hooks, value alignment policies, red-teaming agent behaviors, and post-hoc interpretability. These features will be increasingly critical as agent autonomy grows.
Q9. Are there plans to allow native agent simulation or dry-run testing?
Yes. Future developer tools will include simulation environments for MCP workflows, enabling "dry runs" of multi-agent interactions without triggering real-world actions. This is essential for testing complex workflows before deployment.
Q10. Will MCP support dynamic tool injection or capability discovery at runtime?
The roadmap includes support for agents to dynamically discover and bind to new tools based on current needs or environmental signals. This means agents will become more adaptable, loading capabilities on-the-fly as needed.
Q11. Will MCP support distributed task execution across geographies?
MCP is exploring distributed task orchestration models where tasks can be delegated across servers in different geographic zones, with state sync and consistency guarantees. This enables latency optimization and compliance with data residency laws.
Q12. Can MCP be used in closed-network or air-gapped environments?
Yes. The protocol is designed to support local and offline deployments. In fact, a lightweight “MCP core” mode is being planned that allows essential features to run without internet access, ideal for defense, industrial, and high-security environments.
Q13. Will there be standardized benchmarking for MCP server performance?
The community plans to release performance benchmarking tools that assess latency, throughput, reliability, and resource efficiency of MCP servers, helping developers optimize implementations and organizations make informed choices.
Q14. Is there an initiative to support accessibility (a11y) in MCP-based agents?
Yes. As multimodal agents become mainstream, MCP will include standards for screen reader compatibility, voice-to-text input, closed captioning in streaming, and accessible tool interfaces. This ensures inclusivity in AI-powered interfaces.
Q15. How will MCP support the coexistence of multiple agent frameworks?
Future versions of MCP will provide standard interoperability layers to allow frameworks like LangChain, AutoGen, Haystack, and Semantic Kernel to plug into a shared context space. This will enable tool-agnostic agent orchestration and smoother ecosystem collaboration.
.png)
With organizations increasingly prioritizing seamless issue resolution—whether for internal teams or end customers—ticketing tools have become indispensable. The widespread adoption of these tools has also amplified the demand for streamlined integration workflows, making ticketing integration a critical capability for modern SaaS platforms.
By integrating ticketing systems with other enterprise applications, businesses can enhance automation, improve response times, and ensure a more connected user experience. In this article, we will explore the different facets of ticketing integration, covering what it entails, its benefits, real-world use cases, and best practices for successful implementation.
Ticketing integration refers to the seamless connection between a ticketing platform and other software applications, allowing for automated workflows, data synchronization, and enhanced operational efficiency. These integrations can broadly serve two key functions—internal process optimization and customer-facing enhancements.
Internally, ticketing integration helps businesses streamline their operations by connecting ticketing systems with tools such as customer relationship management (CRM) platforms, enterprise resource planning (ERP) systems, human resource information systems (HRIS), and IT service management (ITSM) solutions. For example, when a customer support ticket is created, integrating it with a CRM ensures that all relevant customer details and past interactions are instantly accessible to support agents, enabling faster and more personalized responses.
Beyond internal workflows, ticketing integration plays a vital role in customer-facing interactions. SaaS providers, in particular, benefit from integrating their applications with the ticketing platforms used by their customers. This allows for seamless issue tracking and resolution, reducing the friction caused by siloed systems.
By automating ticket workflows and integrating support systems, teams can respond to and resolve customer issues much faster. Automated routing ensures that tickets reach the right department instantly, reducing delays and improving overall efficiency.
Example: A telecom company integrates its ticketing system with a chatbot, allowing customers to report issues 24/7. The chatbot categorizes and assigns tickets automatically, reducing average resolution time by 30%.
Manual ticket logging can lead to data discrepancies, miscommunication, and human errors. Ticketing integration automatically syncs information across platforms, minimizing mistakes and ensuring that all stakeholders have accurate and up-to-date records.
Example: A SaaS company integrates its CRM with the ticketing system so that customer details and past interactions auto-populate in new tickets. This reduces duplicate entries and prevents errors like assigning cases to the wrong agent.
Integration breaks down silos between teams by ensuring everyone has access to the same ticketing information. Whether it’s support, sales, or engineering, all departments can collaborate effectively, reducing response times and improving the overall customer experience.
SaaS applications that integrate with customers' ticketing systems offer a seamless experience, making them more attractive to potential users. Customers prefer apps that fit into their existing workflows, increasing adoption rates. Additionally, once users experience the efficiency of ticketing integration, they are more likely to continue using the product, driving customer retention.
Example: A project management SaaS integrates with Jira Service Management, allowing customers to convert project issues into tickets instantly. This integration makes the SaaS tool more appealing to Jira users, leading to higher sign-ups and long-term retention.
Customers and internal teams benefit from instant updates on ticket progress, reducing uncertainty and frustration. This real-time visibility helps teams proactively address issues, avoid duplicate work, and provide timely responses to customers.
Here are a few common data models for ticketing integration data models:
Integrating ticketing systems effectively requires a structured approach to ensure seamless functionality, optimized performance, and long-term scalability. Here are the key best practices developers should follow when implementing ticketing system integrations.
Choosing the appropriate ticketing system is a critical first step in the integration process, as it directly impacts efficiency, customer satisfaction, and overall workflow automation. Developers must evaluate ticketing platforms like Jira, Zendesk, and ServiceNow based on key factors such as automation capabilities, reporting features, third-party integration support, and scalability. A well-chosen tool should align not only with internal team workflows but also with customer-facing requirements, particularly for integrations that enhance user experience and service delivery. Additionally, preference should be given to widely adopted ticketing solutions that are frequently used by customers, as this increases compatibility and reduces friction in external integrations. Beyond tool selection, it is equally important to define clear use cases for integration.
A deep understanding of the ticketing system’s API is crucial for successful integration. Developers should review API documentation to comprehend authentication mechanisms (API keys, OAuth, etc.), rate limits, request-response formats, and available endpoints. Some ticketing APIs offer webhooks for real-time updates, while others require periodic polling. Being aware of these aspects ensures a smooth integration process and prevents potential performance bottlenecks.
Choosing the right ticketing integration methodology is crucial for aligning with business objectives, security policies, and technical capabilities. The integration approach should be tailored to meet specific use cases and performance requirements. Common methodologies include direct API integration, middleware-based solutions, and Integration Platform as a Service (iPaaS), including embedded iPaaS or unified API solutions. The choice of methodology should depend on several factors, including the complexity of the integration, the intended audience (internal teams vs. customer-facing applications), and any specific security or compliance requirements. By evaluating these factors, developers can choose the most effective integration approach, ensuring seamless connectivity and optimal performance.
Efficient API usage is critical to maintaining system performance and preventing unnecessary overhead. Developers should minimize redundant API calls by implementing caching strategies, batch processing, and event-driven triggers instead of continuous polling. Using pagination for large data sets and adhering to API rate limits prevents throttling and ensures consistent service availability. Additionally, leveraging asynchronous processing for time-consuming operations enhances user experience and backend efficiency.
Thorough testing is essential before deploying ticketing integrations to production. Developers should utilize sandbox environments provided by ticketing platforms to test API calls, validate workflows, and ensure proper error handling. Implementing unit tests, integration tests, and load tests helps identify potential issues early. Logging mechanisms should be in place to monitor API responses and debug failures efficiently. Comprehensive testing ensures a seamless experience for end users and reduces the risk of disruptions.
As businesses grow, ticketing system integrations must be able to handle increasing data volumes and user requests. Developers should design integrations with scalability in mind, using cloud-based solutions, load balancing, and message queues to distribute workloads effectively. Implementing asynchronous processing and optimizing database queries help maintain system responsiveness. Additionally, ensuring fault tolerance and setting up monitoring tools can proactively detect and resolve issues before they impact operations.
In today’s SaaS landscape, numerous ticketing tools are widely used by businesses to streamline customer support, issue tracking, and workflow management. Each of these platforms offers its own set of APIs, complete with unique endpoints, authentication methods, and technical specifications. Below, we’ve compiled a list of developer guides for some of the most popular ticketing platforms to help you integrate them seamlessly into your systems:
CRM-ticketing integration ensures that any change made in the ticketing system (such as a new support request or status change) will automatically be reflected in the CRM, and vice versa. This ensures that all customer-related data is current and consistent across the board. For example, when a customer submits a support ticket via a ticketing platform (like Zendesk or Freshdesk), the system automatically creates a new entry in the CRM, linking the ticket directly to the customer’s profile. The sales team, which accesses the CRM, can immediately view the status of the issue being reported, allowing them to be aware of any ongoing concerns or follow-up actions that might impact their next steps with the customer.
As support agents work on the ticket, they might update its status (e.g., “In Progress,” “Resolved,” or “Awaiting Customer Response”) or add important resolution notes. Through bidirectional sync, these changes are immediately reflected in the CRM, keeping the sales team updated. This ensures that the sales team can take the customer’s issues into account when planning outreach, upselling, or renewals. Similarly, if the sales team updates the customer’s contact details, opportunity stage, or other key information in the CRM, these updates are also synchronized back into the ticketing system. This means that when a support agent picks up the case, they are working with the most accurate and recent information.
Collaboration tool-ticketing integration ensures that when a customer submits a support ticket through the ticketing system, a notification is automatically sent to the relevant team’s communication tool (such as Slack or Microsoft Teams). The support agent or team is alerted in real-time about the new ticket, and they can immediately begin the troubleshooting process. As the agent works on the ticket—changing its status, adding comments, or marking it as resolved—updates are automatically pushed to the communication tool.
The integration may also allow for direct communication with customers through the ticketing platform. Support agents can update the ticket in real-time based on communication happening within the chat, keeping customers informed of progress, or even resolving simple issues via a direct message.
Integrating an AI-powered chatbot with a ticketing system enhances customer support by enabling seamless automation for ticket creation, tracking, and resolution, all while providing real-time assistance to customers. When a customer interacts with the chatbot on the support portal or website, the chatbot uses NLP to analyze the query. If the issue is complex, the chatbot automatically creates a support ticket in the ticketing system, capturing the relevant customer details and issue description. This integration ensures that no query goes unresolved, and no customer issue is overlooked.
Once the ticket is created, the chatbot continuously engages with the customer, providing real-time updates on the status of their ticket. As the ticket progresses through various stages (e.g., from “Open” to “In Progress”), the chatbot retrieves updates from the ticketing system and informs the customer, reducing the need for manual follow-ups. When the issue is resolved and the ticket is closed by the support agent, the chatbot notifies the customer of the resolution, asks if further assistance is needed, and optionally triggers a feedback request or satisfaction survey.
Ticketing integration with a HRIS offers significant benefits for organizations looking to streamline HR operations and enhance employee support. For example, when an employee raises a ticket to inquire about their leave balance, the integration allows the ticketing platform to automatically pull relevant data from the HRIS, enabling the HR team to provide accurate and timely responses.
The workflow begins with the employee submitting a ticket through the ticketing platform, which is then routed to the appropriate HR team based on predefined rules or triggers. The integration ensures that employee data, such as job role, department, and contact details, is readily available within the ticketing system, allowing HR teams to address queries more efficiently. Automated responses can be triggered for common inquiries, such as leave balances or policy questions, further speeding up resolution times. Once the issue is resolved, the ticket is closed, and any updates, such as approved leave requests, are automatically reflected in the HRIS.
Read more: Everything you need to know about HRIS API Integration
Integrating a ticketing platform with a payroll system can automate data retrieval, streamline workflows, and provide employees with faster, more accurate responses. It begins when an employee submits a ticket through the ticketing platform, such as a query about a missing payment or a discrepancy in their paycheck. The integration allows the ticketing platform to automatically pull the employee’s payroll data, including payment history, tax details, and direct deposit information, directly from the payroll system. This eliminates the need for manual data entry and ensures that the HR or payroll team has all the necessary information at their fingertips. The ticket is then routed to the appropriate payroll specialist based on predefined rules, such as the type of issue or the employee’s department.
Once the ticket is assigned, the payroll specialist reviews the employee’s payroll data and investigates the issue. For example, if the employee reports a missing payment, the specialist can quickly verify whether the payment was processed and identify any errors, such as incorrect bank details or a missed payroll run. After resolving the issue, the specialist updates the ticket with the resolution details and notifies the employee. If any changes are made to the payroll system, such as reprocessing a payment or correcting tax information, these updates are automatically reflected in both systems, ensuring data consistency. Similarly, if an employee asks about their upcoming pay date, the ticketing platform can automatically generate a response using data from the payroll system, reducing the workload on the payroll team.
Ticketing-e-commerce order management system integration can transform how businesses handle customer inquiries related to orders, shipping, and returns. When a customer submits a ticket through the ticketing platform, such as a query about their order status, a request for a return, or a complaint about a delayed shipment, the integration allows the ticketing platform to automatically pull the customer’s order details—such as order number, purchase date, shipping status, and tracking information—directly from the order management system.
The ticket is then routed to the appropriate support team based on the type of inquiry, such as shipping, returns, or billing. Once the ticket is assigned, the support agent reviews the order details and takes the necessary action. For example, if a customer reports a delayed shipment, the agent can check the real-time shipping status and provide the customer with an updated delivery estimate. After resolving the issue, the agent updates the ticket status and notifies the customer with bi-directional sync, ensuring transparency throughout the process.
As you embark on your integration journey, it is integral to understand the roadblocks that you may encounter. These challenges can hinder productivity, delay response times, and lead to frustration for both engineering teams and end-users. Below, we explore some of the most common ticketing integration challenges and their implications.
A critical factor in the success for ticketing integration is the availability of clear, comprehensive documentation. The integration of ticketing platforms with other systems depends heavily on well-documented API and integration guides. Unfortunately, many ticketing platforms provide limited or outdated documentation, leaving developers to navigate challenges with minimal guidance.
The implications of inadequate documentation are far-reaching:
Error handling is an essential part of any system integration. When integrating ticketing systems with other platforms, it is important for developers to be able to quickly identify and resolve errors to prevent disruptions in service. Unfortunately, many ticketing systems fail to provide detailed and effective error-handling and logging mechanisms, which can significantly hinder the integration process.
Key challenges include:
Read more: API Monitoring and Logging
As organizations grow, so does the volume of data generated through ticketing systems. When an integration is not designed to handle large volumes of data, businesses may experience performance issues such as slowdowns, data loss, or bottlenecks in the system. Scalability is therefore a key concern when integrating ticketing systems with other platforms.
Some of the key scalability challenges include:
In many organizations, different teams use different ticketing tools that are tailored to their specific workflows. Integrating multiple ticketing systems can create complexity, leading to potential data inconsistencies and synchronization challenges.
Key challenges include:
Testing the integration of ticketing systems is critical before deploying them into a live environment. Unfortunately, many ticketing platforms offer limited or restricted access to testing environments, which can complicate the integration process and delay project timelines.
Key challenges include:
Another common challenge in ticketing system integration is compatibility between different systems. Ticketing platforms often use varying data formats, authentication methods, and API structures, making it difficult for systems to communicate effectively with each other.
Some of the key compatibility challenges include:
Once an integration is completed, the work is far from finished. Ongoing maintenance and management are essential to ensure that the integration continues to function smoothly as both ticketing systems and other integrated platforms evolve.
Some of the key maintenance challenges include:
Knit provides a unified ticketing API that streamlines the integration of ticketing solutions. Instead of connecting directly with multiple ticketing APIs, Knit’s AI allows you to connect with top providers like Zoho Desk, Freshdesk, Jira, Trello and many others through a single integration.
Getting started with Knit is simple. In just 5 steps, you can embed multiple CRM integrations into your App.
Steps Overview:
Read more: Getting started with Knit
Choosing the ideal approach to building and maintaining ticketing integration requires a clear comparison. While traditional custom connector APIs require significant investment in development and maintenance, a unified ticketing API like Knit offers a more streamlined approach with faster integration and greater flexibility. Below is a detailed comparison of these two approaches based on several crucial parameters:

Read more: How Knit Works
Below are key security risks and mitigation strategies to safeguard ticketing integrations.
To safeguard ticketing integrations and ensure a secure environment, organizations should employ several mitigation strategies:
When evaluating the security of a ticketing integration, consider the following key factors:
Read more: API Security 101: Best Practices, How-to Guides, Checklist, FAQs
Ticketing integration connects ticketing systems with other software to automate workflows, improve response times, enhance user experiences, reduce manual errors, and streamline communication. Developers should focus on selecting the right tools, understanding APIs, optimizing performance, and ensuring scalability to overcome challenges like poor documentation, error handling, and compatibility issues.
Solutions like Knit’s unified ticketing API simplify integration, offering faster setup, better security, and improved scalability over in-house solutions. Knit’s AI-driven integration agent guarantees 100% API coverage, adds missing applications in just 2 days, and eliminates the need for developers to handle API discovery or maintain separate integrations for each tool.
Curated API guides and documentations for all the popular tools

JazzHR ATS is a purpose-built applicant tracking system designed to simplify and automate hiring for small and mid-sized organizations. It centralizes job posting, applicant management, interview workflows, and compliance tracking into a single system, reducing manual effort and improving hiring velocity.
Beyond its core ATS capabilities, JazzHR provides a well-structured API that allows teams to integrate recruitment data with external HR systems, analytics platforms, background verification tools, and internal workflows. The JazzHR ATS API enables controlled access to hiring data, allowing organizations to extend JazzHR’s capabilities without disrupting existing processes. For teams aiming to operationalize hiring data across systems, the API becomes a critical enabler rather than a nice-to-have.
https://api.resumatorapi.com/v1/activitieshttps://api.resumatorapi.com/v1/activities/{activityID}https://api.resumatorapi.com/v1/applicantshttps://api.resumatorapi.com/v1/applicants/{applicantID}https://api.resumatorapi.com/v1/applicants2jobshttps://api.resumatorapi.com/v1/applicants2jobs/{applicants2jobsID}https://api.resumatorapi.com/v1/categorieshttps://api.resumatorapi.com/v1/categories/{categoriesID}https://api.resumatorapi.com/v1/categories2applicantshttps://api.resumatorapi.com/v1/categories2applicants/{categories2applicantsID}https://api.resumatorapi.com/v1/contactshttps://api.resumatorapi.com/v1/contacts/{contactsID}https://api.resumatorapi.com/v1/fileshttps://api.resumatorapi.com/v1/files/{filesID}https://api.resumatorapi.com/v1/hireshttps://api.resumatorapi.com/v1/jobshttps://api.resumatorapi.com/v1/jobs/{jobID}https://api.resumatorapi.com/v1/noteshttps://api.resumatorapi.com/v1/questionnaire_answershttps://api.resumatorapi.com/v1/questionnaire_answers/pages/{page_id}https://api.resumatorapi.com/v1/questionnaire_questions/questionnaire_id/questionnaire_20240715163409_5EYUGO8YULDRJOAEhttps://api.resumatorapi.com/v1/taskshttps://api.resumatorapi.com/v1/tasks/{taskID}https://api.resumatorapi.com/v1/usershttps://api.resumatorapi.com/v1/users/{userID}1. What are common use cases for the JazzHR ATS API?
Automating applicant ingestion, syncing hiring data to HRIS or payroll systems, building hiring dashboards, and integrating background checks or assessments.
2. How is authentication handled in the JazzHR API?
All endpoints require an API key, passed either as a query parameter or header depending on the endpoint.
3. Can applicants be created and assigned to jobs via API?
Yes. Applicants can be created using the Applicants endpoint and mapped to jobs using the Applicants2Jobs endpoint.
4. Does the API support pagination for large datasets?
Yes. Most list endpoints support pagination with configurable page sizes, typically up to 100 records per page.
5. Can files like resumes and documents be uploaded programmatically?
Yes. The Files API allows uploading Base64-encoded files and linking them to applicants.
6. How can hiring activity be tracked in real time?
The Activities and Tasks endpoints provide detailed logs of user actions, applicant movements, and workflow updates.
7. Is the JazzHR API suitable for enterprise-scale integrations?
It is well-suited for SMB and mid-market scale. For higher volumes, careful rate management and pagination handling are recommended.
While the JazzHR ATS API is powerful, managing authentication, versioning, retries, and long-term maintenance adds operational overhead. Platforms like Knit API abstract these complexities by providing a single, standardized integration layer. With one integration to Knit, teams can access JazzHR data without managing API-specific logic, enabling faster deployment and lower maintenance cost.
The bottom line: if JazzHR is your system of record for hiring, its API is the backbone for scaling recruitment operations across tools, teams, and workflows.

Zoho CRM is a cloud-based customer relationship management platform used to manage leads, contacts, deals, activities, and customer service workflows in one system. Teams typically adopt it to centralize customer data, standardize sales processes, and improve pipeline visibility through reporting and automation.
For most businesses, the real value comes when Zoho CRM does not operate in isolation. The Zoho CRM API enables you to connect Zoho CRM with your website, marketing automation, support desk, ERP, data warehouse, or internal tools, so records stay consistent across systems and core operations run with fewer manual handoffs. This guide breaks down what the API is best suited for, what to plan for in integration, and the key endpoints you can build around.
If you want to avoid building and maintaining the entire integration surface area in-house, Knit API offers a faster route to production. By integrating with Knit once, you can streamline access to Zoho CRM APIs while offloading authentication handling and integration maintenance. This is especially useful when Zoho CRM is one of multiple CRMs or SaaS systems you need to support under a single integration layer.

Zoho Recruit is a cloud-based applicant tracking system built to handle the real mechanics of hiring, candidates, job openings, interviews, submissions, and reviews, without forcing teams into rigid workflows. It’s widely used by HR teams, recruitment agencies, and staffing firms that need control over hiring pipelines, not just a pretty UI.
Where Zoho Recruit really scales is through its API layer. The Zoho Recruit API allows you to plug recruiting data directly into your internal systems, HRIS, payroll, BI tools, CRMs, or custom hiring dashboards, so hiring stops being a siloed function and becomes part of your core operations.
https://recruit.zoho.com/recruit/bulk/v2/readhttps://recruit.zoho.com/recruit/bulk/v2/read/{job_id}https://recruit.zoho.com/recruit/bulk/v2/read/{job_id}/resulthttps://recruit.zoho.com/recruit/bulk/v2/writehttps://recruit.zoho.com/recruit/bulk/v2/write/{job_id}https://recruit.zoho.com/recruit/v2.1/Assessmentshttps://recruit.zoho.com/recruit/v2.1/Assessments/{record_id}https://recruit.zoho.com/recruit/v2/Applications/statushttps://recruit.zoho.com/recruit/v2/Applications/{application_id}/Attachmentshttps://recruit.zoho.com/recruit/v2/Candidates/actions/associatehttps://recruit.zoho.com/recruit/v2/Candidates/actions/import_documenthttps://recruit.zoho.com/recruit/v2/Candidates/{record_id}/actions/add_tagshttps://recruit.zoho.com/recruit/v2/Interviewshttps://recruit.zoho.com/recruit/v2/Interviews/{record_id}/action/cancelhttps://recruit.zoho.com/recruit/v2/JobOpeningshttps://recruit.zoho.com/recruit/v2/Noteshttps://recruit.zoho.com/recruit/v2/Notes/{note_id}https://recruit.zoho.com/recruit/v2/Reviewshttps://recruit.zoho.com/recruit/v2/Reviews/{record_id}https://recruit.zoho.com/recruit/v2/Submissionshttps://recruit.zoho.com/recruit/v2/Submissions/{record_id}/actions/statushttps://recruit.zoho.com/recruit/v2/orghttps://recruit.zoho.com/recruit/v2/settings/moduleshttps://recruit.zoho.com/recruit/v2/settings/fields?module={module_api_name}https://recruit.zoho.com/recruit/v2/settings/custom_views?module={module_api_name}https://recruit.zoho.com/recruit/v2/settings/roleshttps://recruit.zoho.com/recruit/v2/settings/profileshttps://recruit.zoho.com/recruit/v2/{module_api_name}https://recruit.zoho.com/recruit/v2/{module_api_name}/searchhttps://recruit.zoho.com/recruit/v2/{module_api_name}/{record_id}https://recruit.zoho.com/recruit/v2/{module_api_name}?ids={record_id}(India-specific .zoho.in endpoints remain unchanged and should be used for region-bound accounts.)
1. What can I build using the Zoho Recruit API?
Anything from custom ATS dashboards and recruiter tools to HRIS integrations, analytics pipelines, and automated hiring workflows.
2. Does the API support bulk data migration?
Yes. Bulk Read and Bulk Write APIs are designed specifically for large-scale exports, imports, and migrations.
3. How is authentication handled?
All APIs use Zoho OAuth 2.0 with scoped access tokens. Permissions are enforced at both user and module levels.
4. Are there rate limits?
Yes. Rate limits vary by API, with stricter limits on bulk operations to prevent abuse.
5. Can I automate interview scheduling and status changes?
Yes. Interviews, applications, and submissions can all be updated programmatically.
6. Is there support for custom modules?
Yes. Custom modules are treated like first-class citizens and can be accessed via the same API patterns.
7. Can I test integrations safely?
Zoho provides sandbox environments so you can build and validate integrations without touching production data.
Integrating directly with the Zoho Recruit API gives you power, but also complexity around OAuth, retries, schema changes, and long-term maintenance.
If you want speed and reliability without building everything from scratch, Knit lets you integrate with Zoho Recruit once and handle authentication, versioning, error handling, and ongoing upkeep automatically. You focus on product logic. Knit keeps the pipes running.